Reverse Deception: Organized Cyber Threat Counter-Exploitation (98 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

SOFTEL (ASN 50134) ranks highest in use by botnet operators (13 times in eight months) followed by COLO-AS (ASN 196954). By taking a look at what months the ISPs were used, we got a history of certain SpyEye activity, as shown in
Figure 9-21
.
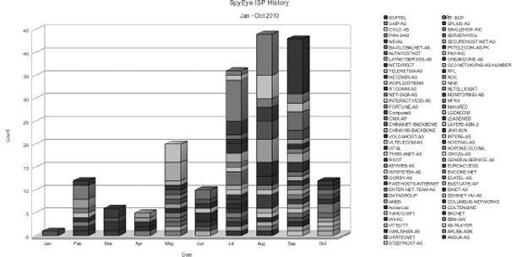
Figure 9-21
ISP usage per month
The graph in
Figure 9-21
illustrates how we can use this information to identify significant patterns. An example is that UAIP-AS (a Ukrainian network, ASN 51306) made a significant appearance in August. If we analyze the specific activity for that ISP, we find this information:
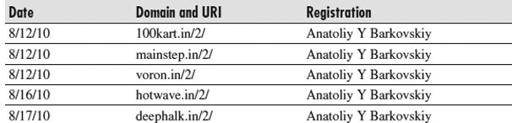
In July, we see the same operator displaying the same pattern using ASN 196814, which is PAN-SAM, a network related to UAIP-AS (also run by PAN-SAM). The operator’s URI pattern remains the same, and he utilizes these ISPs for aggressive malware distribution and CnC use.
By following the trail of convenience for operators (known serial ISPs that enable their malicious activities), this type of analysis allows you to trace backward and track distinct operators.
Aftermath
At the end of a 10-month analysis of over 30 SpyEye botnet CnC servers, the analysis team was able to determine which criminals behind each botnet (almost all being run independently) posed the largest threat to enterprise networks. There were several tied back directly to the author of SpyEye, Gribodemon, and his cohorts and direct customers, who at the time went by the online identities Hiro, Bx1, jb00n, and Vasy. The information was collected and used against the criminals to deny, degrade, and deceive their ability to continue to steal from the innocent. The analysis team was able to provide detailed information for each criminal operating each SpyEye botnet, including the following:
Crimeware infrastructure configuration
Botnet update procedures
Motive and intent of criminal
Personally identifiable information (of the criminal operator)
Login and password for the botnet domain registrar account
Login and password for e-mail accounts the criminal used for alerts
Login and password for virtest accounts (which test SpyEye binaries detection rates)
Login and password for domain blacklist checkers
Login and password for criminal online bank accounts
Login and password for incoming IP addresses (where is the bad guy?)