SpyEye main CP server desktop
You need to run this VM image locally using an open source or commercial version of a VM manager system, such as Virtual Box or VMware.
We also used BurpSuite, developed by Port Swigger (
http://portswigger.net
), which is a Java-based application for testing the security of web applications. This is a highly recommended tool when analyzing the security cyber criminal support infrastructures. Download the free version of BurpSuite, and with the SpyEye CP running locally, run the BurpSuite tool and set it with the following settings in the proxy tab under proxy listeners.
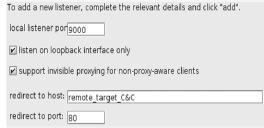
Proxy listeners setting to add new listener
Further down on the same tab, set the “match and replace” for the proxy of the session to overwrite the header request with one that would dupe the remote system into communicating openly between the SpyEye collector and the local CP, as shown here:
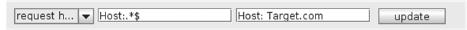
Request header overwrite between the local and remote server
Once these two settings have been made, all requests that are generated locally are sent to the remote server, and due to the nature of Ajax session management, you will be able to manipulate the remote server into responding to a local request. In practice, the vulnerability works, as Ajax is seeing the request coming in to the server, but it cannot distinguish between a remote and local request. Upon generating a local request, the remote server responds and sends all of the remote server information to the local server, seeing it to be a part of the remote infrastructure.
By using this technique, you are provided with
all
of the information stored on the remote CnC server, which is transferred seamlessly to the local CP for full inspection by the analysis team. You also have the data related to the victims that is stored in a SpyEye collector and all of the applicable statistics. The remote server then copies the following files to the local root directory of the web server running the SpyEye CP, which provide even more information related to the criminals’ infrastructure and their current campaign.
 Debug.log (general traffic)
Debug.log (general traffic)
 Error.log (possible leaked IP addresses and other information)
Error.log (possible leaked IP addresses and other information)
 Tasks.log (what it’s doing)
Tasks.log (what it’s doing)
 Backup.sh
Backup.sh
(SQL dump and passwords)
 Config.ini (settings)
Config.ini (settings)
Although you may think what we have done is illegal, it actually is not. The analysis team worked with cyber law legal counsel for several weeks to refine the legal explanation and walk through the processes and procedures of this technique. By following the steps and recommendations covered in
Chapter 5
, we were able to convey the appropriate information for our legal counsel to understand the technique. Per the counsel, we were simply locally requesting remote files on obfuscated directories.
As the local CP in our control was obtained publicly, and the exploitable vulnerability did not affect or alter the state of the remote server, we were provided a legal analysis approving our technique for counter-exploiting criminal servers to learn more about the operators behind the campaigns. You may be surprised that the technique we developed was approved for use by not only our immediate legal counsel, but also by US law enforcement. This being said, we will now dive into the analysis of the data of more than 30 different criminal CnC infrastructures, and examine the habits and practices of the criminal operators to determine the motive, intent, and capability of the criminals behind the campaigns.
About SpyEye
SpyEye is a low-cost and effective do-it-yourself (DIY) Trojan kit with many features. With SpyEye, sorting can be based on infected processes, bot globally unique identifiers (GUIDs), and FTP logins. The configuration requires a standard Linux, Apache, MySQL, and PHP (LAMP) environment. The installation is simple, and the majority of the front-end web code uses Ajax (XML/HTTP) to post the data queries to the viewer.
SpyEye divides itself into two setups: the CnC controller (this houses the statistics and communication with the machines interactively) and the form grabber, which is used to collect the login data and store it in a database for querying. The form grabber and the CnC controller identify themselves to an outside observer via the HTML
tag that most browsers render to be displayed in the middle of the top bar of the browser when accessing the page.<br/><a><span>Figures 9-1<br/></span></a>and<br/><a><span>9-2<br/></span></a>show examples of these <title> tags.<br/></p><p><img src="/files/04/30/61/f043061/public/00139.jpg" /></p><p> <br/></p><p><span>Figure 9-1<br/></span><span>CnC identifier within the <title> tag (CN 1)<br/></span></p><p> <br/></p><p><img src="/files/04/30/61/f043061/public/00036.jpg" /></p><p> <br/></p><p><span>Figure 9-2<br/></span><span>Form grabber identifier within the <title> tag (SYN 1)<br/></span></p><p> <br/></p><p>To access either CN 1 or SYN 1, a password prompt is displayed to authenticate access, as shown in<br/><a><span>Figure 9-3<br/></span></a>.<br/></p><p><img src="/files/04/30/61/f043061/public/00038.jpg" /></p> </div>
<div class="col-xs-12 text-left pagination-container">
<ul class="pagination"><li class="prev"><a href="/read-online-reverse-deception-organized-cyber-threat-counter-exploitation-full/books-93" data-page="92">«</a></li>
<li class="first"><a href="/read-online-reverse-deception-organized-cyber-threat-counter-exploitation-full" data-page="0">1</a></li>
<li class="disabled"><span>...</span></li>
<li><a href="/read-online-reverse-deception-organized-cyber-threat-counter-exploitation-full/books-45" data-page="44">45</a></li>
<li class="disabled"><span>...</span></li>
<li><a href="/read-online-reverse-deception-organized-cyber-threat-counter-exploitation-full/books-89" data-page="88">89</a></li>
<li><a href="/read-online-reverse-deception-organized-cyber-threat-counter-exploitation-full/books-90" data-page="89">90</a></li>
<li><a href="/read-online-reverse-deception-organized-cyber-threat-counter-exploitation-full/books-91" data-page="90">91</a></li>
<li><a href="/read-online-reverse-deception-organized-cyber-threat-counter-exploitation-full/books-92" data-page="91">92</a></li>
<li><a href="/read-online-reverse-deception-organized-cyber-threat-counter-exploitation-full/books-93" data-page="92">93</a></li>
<li class="active"><a href="/read-online-reverse-deception-organized-cyber-threat-counter-exploitation-full/books-94" data-page="93">94</a></li>
<li><a href="/read-online-reverse-deception-organized-cyber-threat-counter-exploitation-full/books-95" data-page="94">95</a></li>
<li><a href="/read-online-reverse-deception-organized-cyber-threat-counter-exploitation-full/books-96" data-page="95">96</a></li>
<li><a href="/read-online-reverse-deception-organized-cyber-threat-counter-exploitation-full/books-97" data-page="96">97</a></li>
<li><a href="/read-online-reverse-deception-organized-cyber-threat-counter-exploitation-full/books-98" data-page="97">98</a></li>
<li class="disabled"><span>...</span></li>
<li><a href="/read-online-reverse-deception-organized-cyber-threat-counter-exploitation-full/books-117" data-page="116">117</a></li>
<li class="disabled"><span>...</span></li>
<li class="last"><a href="/read-online-reverse-deception-organized-cyber-threat-counter-exploitation-full/books-135" data-page="134">135</a></li>
<li class="next"><a href="/read-online-reverse-deception-organized-cyber-threat-counter-exploitation-full/books-95" data-page="94">»</a></li></ul> </div>
<div class=""><div class="col-xs-12"><h2>Other books</h2></div><div class="list-b-item col-xs-12 col-md-6"><svg enable-background="new 0 0 483.254 483.254" viewBox="0 0 483.254 483.254" xmlns="http://www.w3.org/2000/svg">
<g><g id="icon_78_">
<path d="m429.56 386.256v-386.256h-341.513c-18.973 0-34.353 15.38-34.353 34.352v351.904z" fill="#f6b863"/>
<path d="m129.907 0h-41.843c-18.972 0-34.352 15.38-34.352 34.352v400.406l76.213 6.931z" fill="#eaa14e"/>
<path d="m102.197 386.256c-26.785 0-48.499 21.714-48.499 48.499s21.714 48.499 48.499 48.499h327.363c-26.559-36.625-26.559-68.958 0-96.999h-327.363z" fill="#eaa14e"/>
<path d="m409.682 469.34h-307.539c-19.096 0-34.576-15.48-34.576-34.576s15.48-34.576 34.576-34.576h306.047c-2.298 3.598-4.193 7.438-5.652 11.451-.721 1.637-1.312 3.327-1.768 5.057-.873 2.81-1.466 5.7-1.768 8.628-.147 1.638-.301 3.418-.301 5.056-.275 2.926-.174 5.875.301 8.775.147 1.638.442 3.418.743 5.057.589 2.823 1.338 5.799 2.234 8.628.589 1.638 1.179 3.418 1.933 5.056 1.655 3.944 3.583 7.768 5.77 11.444z" fill="#eeefee"/>
<path d="m163.971 53.117h213.622v103.923h-213.622z" fill="#eaa14e"/><path d="m178.845 67.986h183.884v74.18h-183.884z" fill="#f6b863"/>
<path d="m163.971 214.777h213.622v13.855h-213.622z" fill="#eaa14e"/><path d="m163.971 259.814h213.622v13.855h-213.622z" fill="#eaa14e"/>
<path d="m210.387 304.851h120.796v13.855h-120.796z" fill="#eaa14e"/>
<g fill="#ccd0d2">
<path d="m402.516 411.638c-.721 1.637-1.312 3.327-1.768 5.057h-303.661v-5.057z"/><path d="m398.98 425.317c-.147 1.638-.301 3.418-.301 5.056h-301.592v-5.056z"/>
<path d="m399.716 444.205h-302.629v-5.057h301.893c.141 1.639.436 3.442.736 5.057z"/><path d="m403.877 457.913h-306.79v-5.056h304.839c.59 1.608 1.179 3.394 1.951 5.056z"/>
</g>
<path d="m128.174 415.994v36.515l16.242-10.826 16.237 10.826v-36.515z" fill="#ef5261"/>
</g></g>
</svg><div><a href="/read-online-very-wicked-beginnings-full">Very Wicked Beginnings</a> by <span>Ilsa Madden-Mills</span></div></div><div class="list-b-item col-xs-12 col-md-6"><svg enable-background="new 0 0 483.254 483.254" viewBox="0 0 483.254 483.254" xmlns="http://www.w3.org/2000/svg">
<g><g id="icon_78_">
<path d="m429.56 386.256v-386.256h-341.513c-18.973 0-34.353 15.38-34.353 34.352v351.904z" fill="#f6b863"/>
<path d="m129.907 0h-41.843c-18.972 0-34.352 15.38-34.352 34.352v400.406l76.213 6.931z" fill="#eaa14e"/>
<path d="m102.197 386.256c-26.785 0-48.499 21.714-48.499 48.499s21.714 48.499 48.499 48.499h327.363c-26.559-36.625-26.559-68.958 0-96.999h-327.363z" fill="#eaa14e"/>
<path d="m409.682 469.34h-307.539c-19.096 0-34.576-15.48-34.576-34.576s15.48-34.576 34.576-34.576h306.047c-2.298 3.598-4.193 7.438-5.652 11.451-.721 1.637-1.312 3.327-1.768 5.057-.873 2.81-1.466 5.7-1.768 8.628-.147 1.638-.301 3.418-.301 5.056-.275 2.926-.174 5.875.301 8.775.147 1.638.442 3.418.743 5.057.589 2.823 1.338 5.799 2.234 8.628.589 1.638 1.179 3.418 1.933 5.056 1.655 3.944 3.583 7.768 5.77 11.444z" fill="#eeefee"/>
<path d="m163.971 53.117h213.622v103.923h-213.622z" fill="#eaa14e"/><path d="m178.845 67.986h183.884v74.18h-183.884z" fill="#f6b863"/>
<path d="m163.971 214.777h213.622v13.855h-213.622z" fill="#eaa14e"/><path d="m163.971 259.814h213.622v13.855h-213.622z" fill="#eaa14e"/>
<path d="m210.387 304.851h120.796v13.855h-120.796z" fill="#eaa14e"/>
<g fill="#ccd0d2">
<path d="m402.516 411.638c-.721 1.637-1.312 3.327-1.768 5.057h-303.661v-5.057z"/><path d="m398.98 425.317c-.147 1.638-.301 3.418-.301 5.056h-301.592v-5.056z"/>
<path d="m399.716 444.205h-302.629v-5.057h301.893c.141 1.639.436 3.442.736 5.057z"/><path d="m403.877 457.913h-306.79v-5.056h304.839c.59 1.608 1.179 3.394 1.951 5.056z"/>
</g>
<path d="m128.174 415.994v36.515l16.242-10.826 16.237 10.826v-36.515z" fill="#ef5261"/>
</g></g>
</svg><div><a href="/read-online-the-mystery-of-the-headless-horse-full">The Mystery of the Headless Horse</a> by <span>William Arden</span></div></div><div class="list-b-item col-xs-12 col-md-6"><svg enable-background="new 0 0 483.254 483.254" viewBox="0 0 483.254 483.254" xmlns="http://www.w3.org/2000/svg">
<g><g id="icon_78_">
<path d="m429.56 386.256v-386.256h-341.513c-18.973 0-34.353 15.38-34.353 34.352v351.904z" fill="#f6b863"/>
<path d="m129.907 0h-41.843c-18.972 0-34.352 15.38-34.352 34.352v400.406l76.213 6.931z" fill="#eaa14e"/>
<path d="m102.197 386.256c-26.785 0-48.499 21.714-48.499 48.499s21.714 48.499 48.499 48.499h327.363c-26.559-36.625-26.559-68.958 0-96.999h-327.363z" fill="#eaa14e"/>
<path d="m409.682 469.34h-307.539c-19.096 0-34.576-15.48-34.576-34.576s15.48-34.576 34.576-34.576h306.047c-2.298 3.598-4.193 7.438-5.652 11.451-.721 1.637-1.312 3.327-1.768 5.057-.873 2.81-1.466 5.7-1.768 8.628-.147 1.638-.301 3.418-.301 5.056-.275 2.926-.174 5.875.301 8.775.147 1.638.442 3.418.743 5.057.589 2.823 1.338 5.799 2.234 8.628.589 1.638 1.179 3.418 1.933 5.056 1.655 3.944 3.583 7.768 5.77 11.444z" fill="#eeefee"/>
<path d="m163.971 53.117h213.622v103.923h-213.622z" fill="#eaa14e"/><path d="m178.845 67.986h183.884v74.18h-183.884z" fill="#f6b863"/>
<path d="m163.971 214.777h213.622v13.855h-213.622z" fill="#eaa14e"/><path d="m163.971 259.814h213.622v13.855h-213.622z" fill="#eaa14e"/>
<path d="m210.387 304.851h120.796v13.855h-120.796z" fill="#eaa14e"/>
<g fill="#ccd0d2">
<path d="m402.516 411.638c-.721 1.637-1.312 3.327-1.768 5.057h-303.661v-5.057z"/><path d="m398.98 425.317c-.147 1.638-.301 3.418-.301 5.056h-301.592v-5.056z"/>
<path d="m399.716 444.205h-302.629v-5.057h301.893c.141 1.639.436 3.442.736 5.057z"/><path d="m403.877 457.913h-306.79v-5.056h304.839c.59 1.608 1.179 3.394 1.951 5.056z"/>
</g>
<path d="m128.174 415.994v36.515l16.242-10.826 16.237 10.826v-36.515z" fill="#ef5261"/>
</g></g>
</svg><div><a href="/read-online-autumn-winds-full">Autumn Winds</a> by <span>Charlotte Hubbard</span></div></div><div class="list-b-item col-xs-12 col-md-6"><svg enable-background="new 0 0 483.254 483.254" viewBox="0 0 483.254 483.254" xmlns="http://www.w3.org/2000/svg">
<g><g id="icon_78_">
<path d="m429.56 386.256v-386.256h-341.513c-18.973 0-34.353 15.38-34.353 34.352v351.904z" fill="#f6b863"/>
<path d="m129.907 0h-41.843c-18.972 0-34.352 15.38-34.352 34.352v400.406l76.213 6.931z" fill="#eaa14e"/>
<path d="m102.197 386.256c-26.785 0-48.499 21.714-48.499 48.499s21.714 48.499 48.499 48.499h327.363c-26.559-36.625-26.559-68.958 0-96.999h-327.363z" fill="#eaa14e"/>
<path d="m409.682 469.34h-307.539c-19.096 0-34.576-15.48-34.576-34.576s15.48-34.576 34.576-34.576h306.047c-2.298 3.598-4.193 7.438-5.652 11.451-.721 1.637-1.312 3.327-1.768 5.057-.873 2.81-1.466 5.7-1.768 8.628-.147 1.638-.301 3.418-.301 5.056-.275 2.926-.174 5.875.301 8.775.147 1.638.442 3.418.743 5.057.589 2.823 1.338 5.799 2.234 8.628.589 1.638 1.179 3.418 1.933 5.056 1.655 3.944 3.583 7.768 5.77 11.444z" fill="#eeefee"/>
<path d="m163.971 53.117h213.622v103.923h-213.622z" fill="#eaa14e"/><path d="m178.845 67.986h183.884v74.18h-183.884z" fill="#f6b863"/>
<path d="m163.971 214.777h213.622v13.855h-213.622z" fill="#eaa14e"/><path d="m163.971 259.814h213.622v13.855h-213.622z" fill="#eaa14e"/>
<path d="m210.387 304.851h120.796v13.855h-120.796z" fill="#eaa14e"/>
<g fill="#ccd0d2">
<path d="m402.516 411.638c-.721 1.637-1.312 3.327-1.768 5.057h-303.661v-5.057z"/><path d="m398.98 425.317c-.147 1.638-.301 3.418-.301 5.056h-301.592v-5.056z"/>
<path d="m399.716 444.205h-302.629v-5.057h301.893c.141 1.639.436 3.442.736 5.057z"/><path d="m403.877 457.913h-306.79v-5.056h304.839c.59 1.608 1.179 3.394 1.951 5.056z"/>
</g>
<path d="m128.174 415.994v36.515l16.242-10.826 16.237 10.826v-36.515z" fill="#ef5261"/>
</g></g>
</svg><div><a href="/read-online-escape-3-defeat-the-aliens-full">Escape 3: Defeat the Aliens</a> by <span>T. Jackson King</span></div></div><div class="list-b-item col-xs-12 col-md-6"><svg enable-background="new 0 0 483.254 483.254" viewBox="0 0 483.254 483.254" xmlns="http://www.w3.org/2000/svg">
<g><g id="icon_78_">
<path d="m429.56 386.256v-386.256h-341.513c-18.973 0-34.353 15.38-34.353 34.352v351.904z" fill="#f6b863"/>
<path d="m129.907 0h-41.843c-18.972 0-34.352 15.38-34.352 34.352v400.406l76.213 6.931z" fill="#eaa14e"/>
<path d="m102.197 386.256c-26.785 0-48.499 21.714-48.499 48.499s21.714 48.499 48.499 48.499h327.363c-26.559-36.625-26.559-68.958 0-96.999h-327.363z" fill="#eaa14e"/>
<path d="m409.682 469.34h-307.539c-19.096 0-34.576-15.48-34.576-34.576s15.48-34.576 34.576-34.576h306.047c-2.298 3.598-4.193 7.438-5.652 11.451-.721 1.637-1.312 3.327-1.768 5.057-.873 2.81-1.466 5.7-1.768 8.628-.147 1.638-.301 3.418-.301 5.056-.275 2.926-.174 5.875.301 8.775.147 1.638.442 3.418.743 5.057.589 2.823 1.338 5.799 2.234 8.628.589 1.638 1.179 3.418 1.933 5.056 1.655 3.944 3.583 7.768 5.77 11.444z" fill="#eeefee"/>
<path d="m163.971 53.117h213.622v103.923h-213.622z" fill="#eaa14e"/><path d="m178.845 67.986h183.884v74.18h-183.884z" fill="#f6b863"/>
<path d="m163.971 214.777h213.622v13.855h-213.622z" fill="#eaa14e"/><path d="m163.971 259.814h213.622v13.855h-213.622z" fill="#eaa14e"/>
<path d="m210.387 304.851h120.796v13.855h-120.796z" fill="#eaa14e"/>
<g fill="#ccd0d2">
<path d="m402.516 411.638c-.721 1.637-1.312 3.327-1.768 5.057h-303.661v-5.057z"/><path d="m398.98 425.317c-.147 1.638-.301 3.418-.301 5.056h-301.592v-5.056z"/>
<path d="m399.716 444.205h-302.629v-5.057h301.893c.141 1.639.436 3.442.736 5.057z"/><path d="m403.877 457.913h-306.79v-5.056h304.839c.59 1.608 1.179 3.394 1.951 5.056z"/>
</g>
<path d="m128.174 415.994v36.515l16.242-10.826 16.237 10.826v-36.515z" fill="#ef5261"/>
</g></g>
</svg><div><a href="/read-online-shattering-inside-full">Shattering Inside</a> by <span>Lisa Ahne</span></div></div><div class="list-b-item col-xs-12 col-md-6"><svg enable-background="new 0 0 483.254 483.254" viewBox="0 0 483.254 483.254" xmlns="http://www.w3.org/2000/svg">
<g><g id="icon_78_">
<path d="m429.56 386.256v-386.256h-341.513c-18.973 0-34.353 15.38-34.353 34.352v351.904z" fill="#f6b863"/>
<path d="m129.907 0h-41.843c-18.972 0-34.352 15.38-34.352 34.352v400.406l76.213 6.931z" fill="#eaa14e"/>
<path d="m102.197 386.256c-26.785 0-48.499 21.714-48.499 48.499s21.714 48.499 48.499 48.499h327.363c-26.559-36.625-26.559-68.958 0-96.999h-327.363z" fill="#eaa14e"/>
<path d="m409.682 469.34h-307.539c-19.096 0-34.576-15.48-34.576-34.576s15.48-34.576 34.576-34.576h306.047c-2.298 3.598-4.193 7.438-5.652 11.451-.721 1.637-1.312 3.327-1.768 5.057-.873 2.81-1.466 5.7-1.768 8.628-.147 1.638-.301 3.418-.301 5.056-.275 2.926-.174 5.875.301 8.775.147 1.638.442 3.418.743 5.057.589 2.823 1.338 5.799 2.234 8.628.589 1.638 1.179 3.418 1.933 5.056 1.655 3.944 3.583 7.768 5.77 11.444z" fill="#eeefee"/>
<path d="m163.971 53.117h213.622v103.923h-213.622z" fill="#eaa14e"/><path d="m178.845 67.986h183.884v74.18h-183.884z" fill="#f6b863"/>
<path d="m163.971 214.777h213.622v13.855h-213.622z" fill="#eaa14e"/><path d="m163.971 259.814h213.622v13.855h-213.622z" fill="#eaa14e"/>
<path d="m210.387 304.851h120.796v13.855h-120.796z" fill="#eaa14e"/>
<g fill="#ccd0d2">
<path d="m402.516 411.638c-.721 1.637-1.312 3.327-1.768 5.057h-303.661v-5.057z"/><path d="m398.98 425.317c-.147 1.638-.301 3.418-.301 5.056h-301.592v-5.056z"/>
<path d="m399.716 444.205h-302.629v-5.057h301.893c.141 1.639.436 3.442.736 5.057z"/><path d="m403.877 457.913h-306.79v-5.056h304.839c.59 1.608 1.179 3.394 1.951 5.056z"/>
</g>
<path d="m128.174 415.994v36.515l16.242-10.826 16.237 10.826v-36.515z" fill="#ef5261"/>
</g></g>
</svg><div><a href="/read-online-the-big-finish-full">The Big Finish</a> by <span>James W. Hall</span></div></div><div class="list-b-item col-xs-12 col-md-6"><svg enable-background="new 0 0 483.254 483.254" viewBox="0 0 483.254 483.254" xmlns="http://www.w3.org/2000/svg">
<g><g id="icon_78_">
<path d="m429.56 386.256v-386.256h-341.513c-18.973 0-34.353 15.38-34.353 34.352v351.904z" fill="#f6b863"/>
<path d="m129.907 0h-41.843c-18.972 0-34.352 15.38-34.352 34.352v400.406l76.213 6.931z" fill="#eaa14e"/>
<path d="m102.197 386.256c-26.785 0-48.499 21.714-48.499 48.499s21.714 48.499 48.499 48.499h327.363c-26.559-36.625-26.559-68.958 0-96.999h-327.363z" fill="#eaa14e"/>
<path d="m409.682 469.34h-307.539c-19.096 0-34.576-15.48-34.576-34.576s15.48-34.576 34.576-34.576h306.047c-2.298 3.598-4.193 7.438-5.652 11.451-.721 1.637-1.312 3.327-1.768 5.057-.873 2.81-1.466 5.7-1.768 8.628-.147 1.638-.301 3.418-.301 5.056-.275 2.926-.174 5.875.301 8.775.147 1.638.442 3.418.743 5.057.589 2.823 1.338 5.799 2.234 8.628.589 1.638 1.179 3.418 1.933 5.056 1.655 3.944 3.583 7.768 5.77 11.444z" fill="#eeefee"/>
<path d="m163.971 53.117h213.622v103.923h-213.622z" fill="#eaa14e"/><path d="m178.845 67.986h183.884v74.18h-183.884z" fill="#f6b863"/>
<path d="m163.971 214.777h213.622v13.855h-213.622z" fill="#eaa14e"/><path d="m163.971 259.814h213.622v13.855h-213.622z" fill="#eaa14e"/>
<path d="m210.387 304.851h120.796v13.855h-120.796z" fill="#eaa14e"/>
<g fill="#ccd0d2">
<path d="m402.516 411.638c-.721 1.637-1.312 3.327-1.768 5.057h-303.661v-5.057z"/><path d="m398.98 425.317c-.147 1.638-.301 3.418-.301 5.056h-301.592v-5.056z"/>
<path d="m399.716 444.205h-302.629v-5.057h301.893c.141 1.639.436 3.442.736 5.057z"/><path d="m403.877 457.913h-306.79v-5.056h304.839c.59 1.608 1.179 3.394 1.951 5.056z"/>
</g>
<path d="m128.174 415.994v36.515l16.242-10.826 16.237 10.826v-36.515z" fill="#ef5261"/>
</g></g>
</svg><div><a href="/read-online-the-other-side-of-anne-full">The Other Side of Anne</a> by <span>Kelly Stuart</span></div></div><div class="list-b-item col-xs-12 col-md-6"><svg enable-background="new 0 0 483.254 483.254" viewBox="0 0 483.254 483.254" xmlns="http://www.w3.org/2000/svg">
<g><g id="icon_78_">
<path d="m429.56 386.256v-386.256h-341.513c-18.973 0-34.353 15.38-34.353 34.352v351.904z" fill="#f6b863"/>
<path d="m129.907 0h-41.843c-18.972 0-34.352 15.38-34.352 34.352v400.406l76.213 6.931z" fill="#eaa14e"/>
<path d="m102.197 386.256c-26.785 0-48.499 21.714-48.499 48.499s21.714 48.499 48.499 48.499h327.363c-26.559-36.625-26.559-68.958 0-96.999h-327.363z" fill="#eaa14e"/>
<path d="m409.682 469.34h-307.539c-19.096 0-34.576-15.48-34.576-34.576s15.48-34.576 34.576-34.576h306.047c-2.298 3.598-4.193 7.438-5.652 11.451-.721 1.637-1.312 3.327-1.768 5.057-.873 2.81-1.466 5.7-1.768 8.628-.147 1.638-.301 3.418-.301 5.056-.275 2.926-.174 5.875.301 8.775.147 1.638.442 3.418.743 5.057.589 2.823 1.338 5.799 2.234 8.628.589 1.638 1.179 3.418 1.933 5.056 1.655 3.944 3.583 7.768 5.77 11.444z" fill="#eeefee"/>
<path d="m163.971 53.117h213.622v103.923h-213.622z" fill="#eaa14e"/><path d="m178.845 67.986h183.884v74.18h-183.884z" fill="#f6b863"/>
<path d="m163.971 214.777h213.622v13.855h-213.622z" fill="#eaa14e"/><path d="m163.971 259.814h213.622v13.855h-213.622z" fill="#eaa14e"/>
<path d="m210.387 304.851h120.796v13.855h-120.796z" fill="#eaa14e"/>
<g fill="#ccd0d2">
<path d="m402.516 411.638c-.721 1.637-1.312 3.327-1.768 5.057h-303.661v-5.057z"/><path d="m398.98 425.317c-.147 1.638-.301 3.418-.301 5.056h-301.592v-5.056z"/>
<path d="m399.716 444.205h-302.629v-5.057h301.893c.141 1.639.436 3.442.736 5.057z"/><path d="m403.877 457.913h-306.79v-5.056h304.839c.59 1.608 1.179 3.394 1.951 5.056z"/>
</g>
<path d="m128.174 415.994v36.515l16.242-10.826 16.237 10.826v-36.515z" fill="#ef5261"/>
</g></g>
</svg><div><a href="/read-online-nights-of-awe-full">Nights of Awe</a> by <span>Harri Nykanen</span></div></div><div class="list-b-item col-xs-12 col-md-6"><svg enable-background="new 0 0 483.254 483.254" viewBox="0 0 483.254 483.254" xmlns="http://www.w3.org/2000/svg">
<g><g id="icon_78_">
<path d="m429.56 386.256v-386.256h-341.513c-18.973 0-34.353 15.38-34.353 34.352v351.904z" fill="#f6b863"/>
<path d="m129.907 0h-41.843c-18.972 0-34.352 15.38-34.352 34.352v400.406l76.213 6.931z" fill="#eaa14e"/>
<path d="m102.197 386.256c-26.785 0-48.499 21.714-48.499 48.499s21.714 48.499 48.499 48.499h327.363c-26.559-36.625-26.559-68.958 0-96.999h-327.363z" fill="#eaa14e"/>
<path d="m409.682 469.34h-307.539c-19.096 0-34.576-15.48-34.576-34.576s15.48-34.576 34.576-34.576h306.047c-2.298 3.598-4.193 7.438-5.652 11.451-.721 1.637-1.312 3.327-1.768 5.057-.873 2.81-1.466 5.7-1.768 8.628-.147 1.638-.301 3.418-.301 5.056-.275 2.926-.174 5.875.301 8.775.147 1.638.442 3.418.743 5.057.589 2.823 1.338 5.799 2.234 8.628.589 1.638 1.179 3.418 1.933 5.056 1.655 3.944 3.583 7.768 5.77 11.444z" fill="#eeefee"/>
<path d="m163.971 53.117h213.622v103.923h-213.622z" fill="#eaa14e"/><path d="m178.845 67.986h183.884v74.18h-183.884z" fill="#f6b863"/>
<path d="m163.971 214.777h213.622v13.855h-213.622z" fill="#eaa14e"/><path d="m163.971 259.814h213.622v13.855h-213.622z" fill="#eaa14e"/>
<path d="m210.387 304.851h120.796v13.855h-120.796z" fill="#eaa14e"/>
<g fill="#ccd0d2">
<path d="m402.516 411.638c-.721 1.637-1.312 3.327-1.768 5.057h-303.661v-5.057z"/><path d="m398.98 425.317c-.147 1.638-.301 3.418-.301 5.056h-301.592v-5.056z"/>
<path d="m399.716 444.205h-302.629v-5.057h301.893c.141 1.639.436 3.442.736 5.057z"/><path d="m403.877 457.913h-306.79v-5.056h304.839c.59 1.608 1.179 3.394 1.951 5.056z"/>
</g>
<path d="m128.174 415.994v36.515l16.242-10.826 16.237 10.826v-36.515z" fill="#ef5261"/>
</g></g>
</svg><div><a href="/read-online-wolf-winter-full">Wolf Winter</a> by <span>Cecilia Ekbäck</span></div></div><div class="list-b-item col-xs-12 col-md-6"><svg enable-background="new 0 0 483.254 483.254" viewBox="0 0 483.254 483.254" xmlns="http://www.w3.org/2000/svg">
<g><g id="icon_78_">
<path d="m429.56 386.256v-386.256h-341.513c-18.973 0-34.353 15.38-34.353 34.352v351.904z" fill="#f6b863"/>
<path d="m129.907 0h-41.843c-18.972 0-34.352 15.38-34.352 34.352v400.406l76.213 6.931z" fill="#eaa14e"/>
<path d="m102.197 386.256c-26.785 0-48.499 21.714-48.499 48.499s21.714 48.499 48.499 48.499h327.363c-26.559-36.625-26.559-68.958 0-96.999h-327.363z" fill="#eaa14e"/>
<path d="m409.682 469.34h-307.539c-19.096 0-34.576-15.48-34.576-34.576s15.48-34.576 34.576-34.576h306.047c-2.298 3.598-4.193 7.438-5.652 11.451-.721 1.637-1.312 3.327-1.768 5.057-.873 2.81-1.466 5.7-1.768 8.628-.147 1.638-.301 3.418-.301 5.056-.275 2.926-.174 5.875.301 8.775.147 1.638.442 3.418.743 5.057.589 2.823 1.338 5.799 2.234 8.628.589 1.638 1.179 3.418 1.933 5.056 1.655 3.944 3.583 7.768 5.77 11.444z" fill="#eeefee"/>
<path d="m163.971 53.117h213.622v103.923h-213.622z" fill="#eaa14e"/><path d="m178.845 67.986h183.884v74.18h-183.884z" fill="#f6b863"/>
<path d="m163.971 214.777h213.622v13.855h-213.622z" fill="#eaa14e"/><path d="m163.971 259.814h213.622v13.855h-213.622z" fill="#eaa14e"/>
<path d="m210.387 304.851h120.796v13.855h-120.796z" fill="#eaa14e"/>
<g fill="#ccd0d2">
<path d="m402.516 411.638c-.721 1.637-1.312 3.327-1.768 5.057h-303.661v-5.057z"/><path d="m398.98 425.317c-.147 1.638-.301 3.418-.301 5.056h-301.592v-5.056z"/>
<path d="m399.716 444.205h-302.629v-5.057h301.893c.141 1.639.436 3.442.736 5.057z"/><path d="m403.877 457.913h-306.79v-5.056h304.839c.59 1.608 1.179 3.394 1.951 5.056z"/>
</g>
<path d="m128.174 415.994v36.515l16.242-10.826 16.237 10.826v-36.515z" fill="#ef5261"/>
</g></g>
</svg><div><a href="/read-online-the-man-who-murdered-god-full">The Man Who Murdered God</a> by <span>John Lawrence Reynolds</span></div></div></div>
<!--er-->
</div>
</div>
<div class="row" style="margin-top: 15px;">
</div>
</div>
</div>
<footer class="footer">
<div class="container">
<p class="pull-left">
© READ ONLINE FREE 2015 - 2025 Contact for me readonlinefreenet@gmail.com </p>
<p class="pull-right">
<!--LiveInternet counter-->
<script type="text/javascript">
document.write("<a href='//www.liveinternet.ru/click' "+
"target=_blank><img src='//counter.yadro.ru/hit?t50.6;r"+
escape(document.referrer)+((typeof(screen)=="undefined")?"":
";s"+screen.width+"*"+screen.height+"*"+(screen.colorDepth?
screen.colorDepth:screen.pixelDepth))+";u"+escape(document.URL)+
";h"+escape(document.title.substring(0,150))+";"+Math.random()+
"' alt='' title='LiveInternet' "+
"border='0' width='31' height='31'><\/a>")
</script>
<!--/LiveInternet-->
</p>
</div>
</footer>
<script src="/assets/ba91f165/jquery.js?v=1529425591"></script>
<script src="/assets/618ab67e/yii.js?v=1529414259"></script>
<script src="/js/site.js?v=1722099411"></script>
<script src="/assets/5e1636ad/js/bootstrap.js?v=1529424553"></script>
</body>
</html>



Debug.log (general traffic)
Error.log (possible leaked IP addresses and other information)
Tasks.log (what it’s doing)
Backup.sh
Config.ini (settings)