Reverse Deception: Organized Cyber Threat Counter-Exploitation (95 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

Figure 9-3
SpyEye password prompt
Latest SpyEye findings reveal certain botnet operators “skinning” their web panel, as shown in
Figure 9-4
. This demonstrates a level of care for their infrastructure.
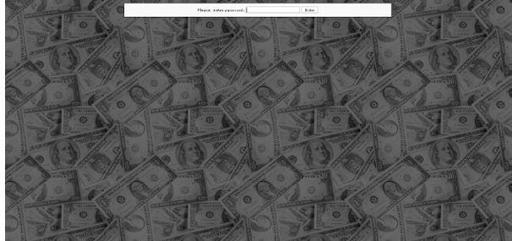
Figure 9-4
“Show me the money” skin
Features of the CnC portion of the web panel include FTP back connect, SOCKS5, code insertion, binary uploads, task monitoring, global statistics, and settings, as shown in
Figure 9-5
.

Figure 9-5
CnC portion of the web panel
Binary Update Function
The binary update function is used to continuously update the bots within the network. Further analysis indicates that this activity happens frequently, at minimum on a daily basis. The purpose of this function is to replace binaries that are unknown to the antivirus community, since the updates are not distributed in the wild via exploits, but internally through the tunnel created between the CnC back end and the operator. Further investigation enables us to identify the new MD5s updated to the bots and reveals how many active bots are receiving updates, as shown in
Figure 9-6
.

Figure 9-6
Real-time update log identifying the new MD5 and the originating MD5
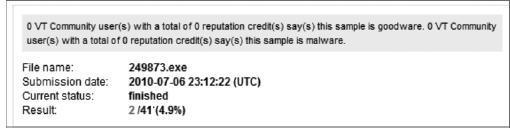
Figure 9-7
MD5 a3fe1f59d8d72699ad342adb992ba450 with 4.9 percent identification according to VirusTotal
Up Sell
Within the SYN 1 form grabber panel, a few features have been updated for version 1.2, including a private certificate stealer, as shown in
Figure 9-8
. This feature allows the botnet operator to request certificates from the controlled bots. Also available is a specific Bank of America grabber. Both of these features require the buyers of the malware DIY kit to pay extra if they desire these features.
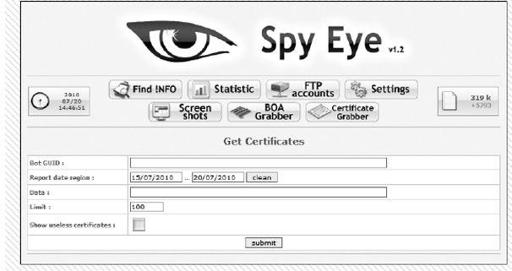
Figure 9-8
Form grabber panel
Backdoor Access
Within the CN 1 panel, there are FTP back connect and SOCKS5 controls designed for miscellaneous use, such as remote administration and sending spam. For each bot with SOCKS5 availability, the server binds a unique port on the CnC server for the botnet operators to perform a reverse connection with the infected host, as shown in
Figure 9-9
.
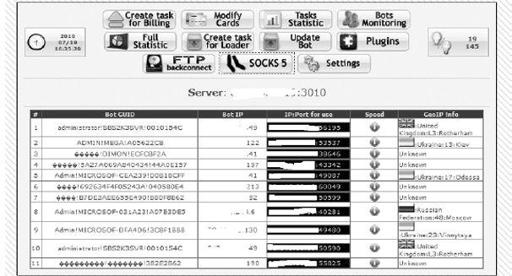
Figure 9-9
SOCKS5 reverse connection status
Statistics and Data Collection
A common trend in many other botnet control panels is the geographical IP address location and version tracking, and SpyEye follows suit, as shown in
Figure 9-10
.
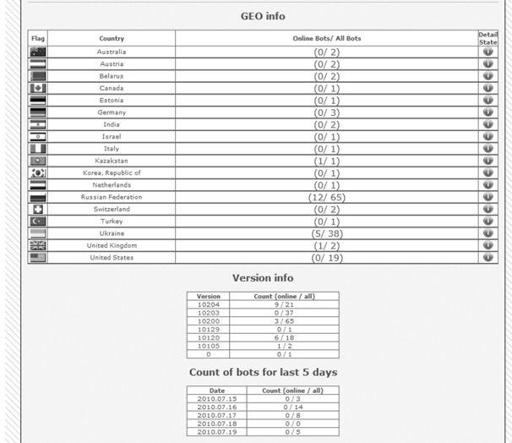
Figure 9-10
Geographical IP address and version tracking
Other statistics acquired are infected operating system versions, Internet Explorer versions, and user type:
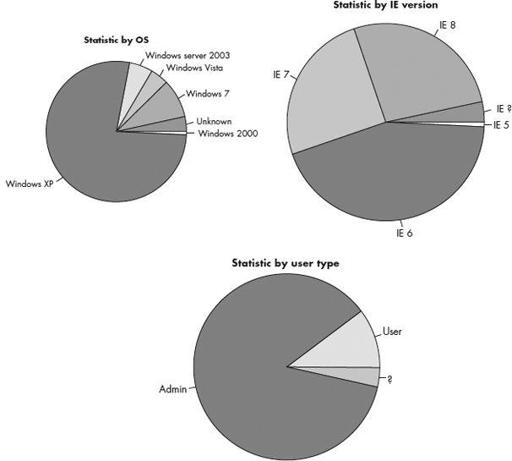
The latest SpyEye malware also enumerates the software information that exists on the victim hosts, as shown in
Figure 9-11
.

Figure 9-11
Enumerated software on an infected host
In addition, check boxes have been added to the stolen data query page, enabling wildcard lookups with the LIKE? option for bot IDs, as shown in
Figure 9-12
. These features were likely added to enable granularity for each query.
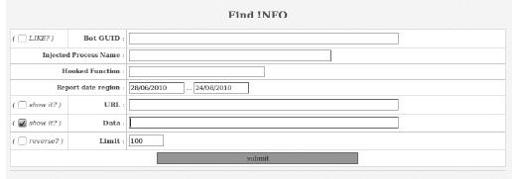
Figure 9-12
Lookup options
SpyEye’s evolution is progressing rapidly, and the success rate of the malware itself appears to be increasing quietly yet effectively. Combined with impactful distribution campaigns, this malware is an up-and-coming contender in the ongoing threats plaguing the Internet.
Traffic, Targets, and Taxonomy
So far, we’ve discussed many of SpyEye’s specific features and demonstrated its rapid evolution, similar to the infamous Zeus malware that scourges the Internet in a highly aggressive manner. Now we will focus on the following topics:
Traffic analysis of the CnC, including configurations and binary updates