Reverse Deception: Organized Cyber Threat Counter-Exploitation (89 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

Are they vulnerable to common attacks, such as cross-site scripting and SQL injection?
Are any of these applications “homegrown,” and are you confident that they were developed with security in mind?
Do the configurations of these applications lend themselves to being an easy target?
How Are Your Passwords?
While you may have a robust password enforcement policy on your hosts and network, some are not so fortunate. Your users’ passwords are the gateway into your network.
Usernames can be discovered pretty easily: just look at your e-mail addresses. With one half of the battle down, there’s only one more piece to complete that username/password combination to gain access to your network. As such, it is imperative that passwords be as secure as possible. While enforcing good passwords will not solve all of your problems, a password is one of those targets that your attacker will pine for.
Table 8-7
lists some of the tools that can help you in your quest for password security.
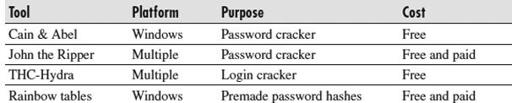
Table 8-7
Password Checking Tools
These tools work as follows:
Cain & Abel
This is one of those tools you should definitely have in your toolbox. This Windows-based tool can crack passwords in Windows SAM files, sniff your network to recover passwords, and do a wide variety of other things.
Figure 8-11
shows an example of Cain & Abel in use. Download this tool at
www.oxid.it/cain.html
.
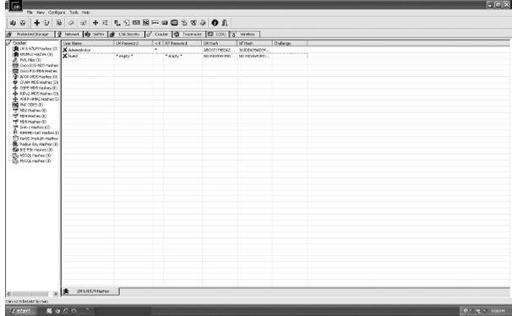
Figure 8-11
Cain & Abel revealing no password for the Guest account
John the Ripper
This tool works on multiple platforms and also provides the ability to check the strength of your users’ passwords. For more information and to download this tool, visit
www.openwall.com/john/
.
THC-Hydra
This is a tool designed for Unix-based (or emulated) platforms that can perform password cracking attacks against multiple network protocols. If you need to check the passwords used by users on services running across your network, give this one a shot. Find out more about this tool and download it at
www.thc.org/thc-hydra/
.
Rainbow tables
This is not actually a tool, but a database of precomputed passwords that can be used to check your Windows-based passwords that are not calculated with a salt (random value). You can actually purchase very extensive rainbow tables to use as another asset in your toolbox. One site that can provide tools and tables is
www.freerainbowtables.com/
.
What Are You Looking For?
Check the following:
As obvious as it sounds, was the program able to crack any of your passwords?
Did you notice any accounts you don’t recognize?
This is a common tactic for your attacker. Get in and create an inconspicuous account to facilitate persistent access.