Reverse Deception: Organized Cyber Threat Counter-Exploitation (84 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

Honeynet Training
A honeynet team must be properly trained in order to fully understand the possible components, scenarios, outcomes, goals/objectives, and missions that honeynets can provide an organization. Currently, the following training courses are available:
SANS offers honeynet workshops, which are generic courses based on the public honeynet tool suites.
Sean Bodmer offers 100 Acre Wood Boot Camp, which is an operationally focused, five-day honeynet boot camp based on over eight years of production honeynet deployment support for various organizations. The boot camp can also be broken down into several individual courses.
Honeynet Objectives
An enterprise honeynet or grid project should provide the capabilities to observe the tools, tactics, procedures, and motives used by adversaries attacking the organization(s) you are protecting by monitoring, recording, and analyzing unauthorized traffic traversing simulated networks.
Based on information observed, the following are common honeynet objectives:
Develop countermeasures to defend against attacks.
Deter potential attacks against operations, networks, and systems by providing a more target-rich environment.
Allow full compromise analysis without operational impacts.
Collect session-level intelligence of actors on live hosts to increase the understanding and intent of malicious activities.
Table 8-3
shows examples of types of Gen III honeynet solutions ranging from low interaction to high interaction based suites. As you can see, high interaction is more for the active engagement of a state-sponsored cyber threat or other highly organized group. Low-interaction honeynets are best to serve as an early warning or scanning detection engine. Honeyclients can be used to analyze websites your users are visiting to see if any of them have successfully exploited and modified settings of a system. In our years of practice, we strongly recommend the build you deploy for your Honeyclient should be your own organization’s system build.
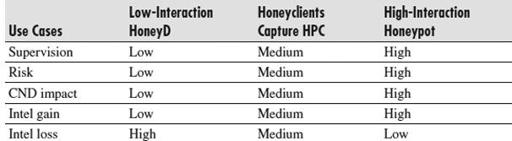
Table 8-3
Honeynet Risk/Benefit Matrix
This will always let you know if your corporate build has exploitable vulnerabilities or if your build is missing a protection measure or setting. If your organization has a system build and you automate a honeyclient where you could pass all of your user local area network DNS traffic analysis engine, this honeyclient would then analyze and determine which of your users could have been or might be infected and could be sending information out of your network to organized opportunistic or targeted criminals.
Honeynet Risks and Issues
Honeynets can be a powerful tool. They allow you to collect extensive information on a variety of threats. To obtain this information, you need to allow attackers and malicious code access—potentially privileged access—to your honeypots. As a result, the price you pay for this capability is risk. Any technology developed by a human can also be defeated by a human.
Risk means different things to different organizations. You will need to identify which risks are important to you. Also, organizations have different thresholds for risk. We cannot determine what is right and wrong for you. Your organization must make those policy decisions for itself. All we can do is help make you aware of the risks.
NOTE
We will not address legal issues of honeypots, or specifically honeynets. That is specific to your country and organization. It is recommended that you consult your organization’s legal counsel for more information, especially in reference to privacy or liability issues.
Four general areas are associated with risk:
Harm
Harm is when a honeynet is used to attack or harm other, non-honeynet systems. For example, an attacker may break into a honeynet, and then launch an outbound attack never seen before, successfully harming or compromising its intended victim. Data control is the primary means of mitigating this risk. Multiple layers of data control are put in place to make it more difficult for the attacker to cause damage. However, there is no guaranteed method to ensure that a honeynet cannot be used to attack or harm someone else. No matter what mechanisms are put in place, an attacker can eventually bypass them. Your organization will need to decide how much risk it is willing to assume. For low-risk organizations, you may want to minimize the activity allowed outbound (to zero, perhaps). For organizations with greater risk thresholds, you may decide to allow greater outbound activity.
Detection
Once the true identity of a honeynet has been identified, its value is dramatically reduced. Attackers can ignore or bypass the honeynet, eliminating its capability for capturing information. Perhaps even more dangerous is the threat that an attacker can introduce false or bogus information into a honeynet, misleading your data analysis. For example, with local access to the honeynet, an attacker armed with the proper skills and tools can potentially identify that a honeynet is in place, and may even identify the honeynet data control and/or data capture mechanisms themselves.
