Reverse Deception: Organized Cyber Threat Counter-Exploitation (119 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers


Vetting Your Operations
When working on an operation, you need to know whether it is working. Well, how do you go about checking this?
You perform the overall vetting of your operation using a bottom-up approach. You start at the bottom (tactical or what you need to address
first
) because that is where all the magic happens, and then work your way up to the overall management and executive level.
For the purpose of continuing with our pseudo-military terminology, we are going to approach this using the observe, orient, decide, and act (OODA) model for the sake of breaking down your operation into a digestible framework.
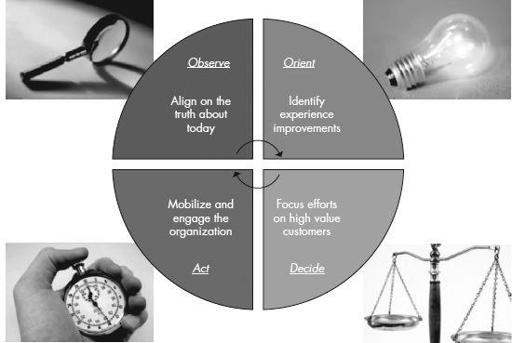
By using the OODA loop process, your operations will be easier to conduct, maintain, and manage from the technical implementation level up to the highest levels of your effort.
If you think about an operation surrounding a persistent threat, a human (your focus) on the other end of the keyboard reacts the same way another human might. The people who are controlling the active campaign against your enterprise will also be interpreting data the same way, as follows:
Observe the current state of their campaign and their crimeware’s actions.
Orient themselves to the output or data (product) of their campaign.
Decide which areas need more work, where to move, or what to do next.
Act on those decisions and continue actions as planned. Your effort’s processes will be logically similar in nature:
Now you have the initial intrusion that was
observed
or discovered that led to the opening of your investigation, which is a technical event and possible business-impact event (loss of intellectual property or resources).
Next you have the analysis you performed on the systems that were affected by the event/intrusion, which needs analysis and
orientation
to understand what is or has occurred.
Then you must identify whether the intrusion/event was targeted or opportunistic and
decide
what to do. This generally leads to a few actions, such as immediate remediation, attempting to block the threat, or possible engagement of the active threat.
Once you decide which avenue to take, the team it is passed off to will
act
on the provided recommended steps. For the sake of this book, we are going to choose the engagement of the active threat approach. If your desire is to simply remediate or attempt blocking, then you can refer to a standard incident response or network defense process, which can be found throughout numerous sites on the Internet.
When validating an operation, one of the first rules to follow is not to look at your focus (the target of your operations) through a mirror. What the focus may or may not do is very likely not the actions you would take in the same situation. Therefore, in order to validate your operation, you must keep in mind your goals, which led you down this path.
As we consider how the operation has proceeded, it is also useful to view the OODA loop through the eyes of the adversary/focus. This will provide you with a greater understanding of whether your operation is going as planned or you need to make modifications to meet your objective.
Is your focus
observing
what you want the focus to see?
Has the threat
oriented
himself to the environment, which you have allowed him to see? Has the threat already mapped all of your network? Has the threat figured out where you store all of your critical assets?