Reverse Deception: Organized Cyber Threat Counter-Exploitation (55 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

Threat (Attacker) Tradecraft


N
ow we will dive into the tradecraft used by threats (your adversaries). They come in many forms and will use many guises to remain persistent.
In this chapter, we are going to cover not only some of the vectors of attack, but also the state of the threat’s underground economy and some of the more interesting methods and tactics used by threats to distribute their “booty and bling” from your enterprise to make the most bang for their buck. Some of the more persistent criminal groups will even use tactics similar to those of the more advanced SSCTs, simply to maintain access to your resources.

Threat Categories
We can divide threats into two primary categories:
Targeted
Your personnel or organizational information and resources are desired to meet a specific collection requirement for monetary or espionage purposes.
Opportunistic (target of opportunity or not targeted)
Your systems become infected by common means and methods (such as client-side exploits and malicious executables), and were used and operated by organized criminals using commonly available crimeware that is used to infect numerous industries and systems for opportunistic monetary gain.
With these two fundamental starting points, you can understand more about the threat operating within your enterprise. There are some tricky things you will need to identify when you see them occur. One of the primary concepts we will discuss is subleasing of criminal botnets. This is when a portion of a threat operator’s botnet is subleased to a third party for a period of time for a specific purpose. If you are interested, you can find out more about this topic through some of the public knowledge sources and underground forums discussed in
Chapter 3
(if they do not shut down after this book is published). On some of these sites, you can see subleasing openly discussed, detailed, and offered to the highest bidder. On some of the underground forums and IRC channels, you’ll see cyber criminals actually trying to sell specific systems they have gained access to.
According to Symantec, less than 1 percent of all global malware is targeted against world governments, and those families and variants are the most dangerous. The other 99 percent is based on opportunistic crimeware, which can be used for targeted attacks if filtered through the appropriate channels. This happens when an opportunistic threat identifies a specific victim’s value, such as a large corporation of value “RSA” (
rsa.com
) or a government entity such as the DoD (dod.mil), which are considered of high value on the underground criminal market. When high-profile organizations such as these become victims of opportunistic cyber criminals, access to their systems is generally sold on the underground black market for large sums of money.
Subleasing can range from a one-off single system scenario all the way up to hundreds of thousands of systems under the control of a single threat operator (which can be an individual or group).
In a typical social network, a systematic circle of trust is built between friends, family, peers, and colleagues. The same is true for criminal operators. They would not have been able to evolve and prosper over the decades without a circle of trust. In a number of the underground forums, you can see the actual status, reputations, rankings, views, and ratings of some of these threat operators. In the following example of such a forum, you can see VipVince is Ownage (this means to own) and has a rating of five stars, where the other posters do not (isn’t he the Staff of the website?).
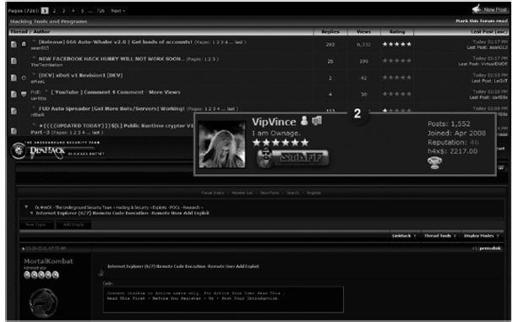
Underground social networking forum illustrating the trust of one’s digital identity by others
Now if you were a criminal and looking to do some business, who would you be more inclined to hook up with? You would choose the guy with the best rating and most views, right? Put on your thinking cap. When you buy anything, from personal to professional goods, you consider the rating of the product, its benefits, reliability, and so on. Criminals, being human, do the exact same thing.
Let’s dig into the types of attacks, targeted and opportunistic, and how to tell which one is occurring.
Targeted Attacks
Targeted attacks are generally associated with cyber espionage and cyber warfare. They include personal, corporate, and government-sponsored attacks against a specific target. The motives and objectives vary, but someone almost always desires to cause a particular network some level of pain or damage by stealing something critical or sensitive to that organization. These attacks can be the most damaging, as the threat is directing generally a large amount of resources to perform reconnaissance, exploitation, infiltration, and persistence to deny, disrupt, degrade, deceive, and/or destroy components of your enterprise.
Targeted attacks can vary in severity and be attributed to individuals or groups. Most international-level governments know exactly who is behind every breach after lengthy periods of analysis and investigation, but it is only spoken about behind closed doors or in classified environments. Sometimes the work is carried out directly by an individual or group, and sometimes the actions are performed by someone who has nothing to do with the threat’s motives or objectives, and simply provides the access needed to get a foothold on your enterprise.
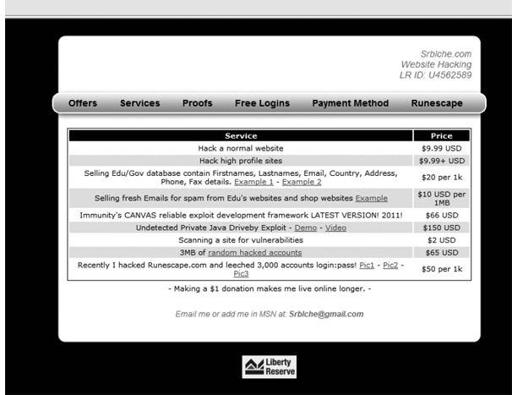
Group offering targeted attacks and ser vices
Most organizations and governments experience targeted attacks regularly, as their enterprises contain high-value information, which is a sad thing. One of the reasons we have put this book together is to introduce the tools and techniques you can use to turn the tides on these criminals with minimal impact on your organization’s operations.
We have worked on countless targeted attacks for numerous customers, and they all had the same basic question when the proverbial crap hit the fan: What do we do now? First, you need to understand what your attackers are after (information or money) and how they are getting out (HTTP, FTP, SSH, SSL, or some other method) of your enterprise. A targeted attacker will spend weeks or longer crafting plans and poking around your enterprise’s locations and points of presence to identify exploitable vulnerabilities. Sometimes you will not be able to detect the activity until it is too late. But being able to respond to attacks appropriately is the important part of remediating a targeted attack. We will talk about that in later chapters, but keep the “What do we do now?” question in mind, and by the end of the book, you will completely get it.
Targeted Subleasing
So let’s talk a little about targeted subleasing. Every hacker/threat/adversary/organized criminal has enough common sense to know when they have struck gold, especially when they have hacked their way into a system of high value. For example, the following is a screenshot of an actual site, discovered in late January 2011, openly selling specific access to third parties (other criminal entities). This screenshot shows a criminal selling specific accounts to various high-value target sites. After making a purchase, a criminal can upload an exploit kit. Based on the volumes of traffic per day to each site, one can easily measure the number of specific victims of that organization or other trusted entities of that victim organization.