Reverse Deception: Organized Cyber Threat Counter-Exploitation (59 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

Botnet operator (goonies)
This group is made up of the true goons of the operation, who generally make a regular salary per week based on their level in the team and the responsibilities they hold for carrying out daily operations of the criminal infrastructure. Their tasks can include updating the bots, data mining on the stolen data, splitting up botnets for subleasing, and so on. Running a botnet is akin to maintaining a cloud computing infrastructure, except for the fact that it’s illegal. This level of the team can consist of anywhere from one to more than a dozen individuals working together.
Distribution provider (infector)
This group generally runs exploit packs in teams and is made up of proficient web application security-inclined individuals. These exploit packs can range in functionality, but all are intended to provide the ability to infect victims’ machines by using locally driven exploits against the operating system, browser, and/or third-party plug-ins. (Exploit packs are discussed later in this chapter.)
Resilience provider (resurrectors)
This component of the criminal team works to ensure the criminal infrastructure does not go down, and if it does, to get it back up as fast as possible. For example, the Ghost Buster network mentioned in the next section would be a service a resilience provider would use to ensure continuity of the criminal network. Open source tools also can be used to help resilience providers in ways that may or may have not been the intentions of the developers of these tools. For example, an academic team created AV Tracker (
www.avtracker.info
), which informs the public of IP addresses of Internet security companies. Lists like these can be used by criminals to ensure their malware does not activate when routed to and from these network ranges. When the other shoe drops on the criminal’s networks, this part of the team is held responsible for getting the criminal’s money, making machine backups, and churning illegal activities. The resilience provider is not only the last line of defense, but can also be used as a part of the persistence methodology that is so commonly used today.
As you can see, several groups operate independently. But in the end, they all have access to your information and have the ability to selectively pick out specific networks of interest for sale to targeted criminal or intelligence groups. There is also the chance that one of the members of any of these groups secretly works for an intelligence service or agency, or is being paid unofficially as a confidential informant to an intelligence collection group.

Criminal Tools and Techniques
Now that you understand the modern criminal’s team breakdown, let’s look at some of the tools and techniques leveraged against us daily. These include the use of legitimate groups offering legitimate services, which are abused or leveraged for malicious purposes.
Tailored Valid Services
Ghost Busters (stealing a copyright or trademark from someone we are fairly certain) offers a service of blacklist notification to customers. The concept is that once a domain is put on any public blacklist, this service will notify customers of specific domains and IP addresses, both good and bad. This type of service is legitimate but is also highly useful to criminals, as they need to know quickly when their CnC domains have been added to public blacklists so the criminals know when they should update their bots, Trojans, or worms with new domains or IP addresses to use once the older domains have been identified as malicious or actively abused or hacked. The following are two screenshots of just one example of such a service. These are associated with a small organization that is still up and running as of May 2012, with a server load of 51 percent. The URL to this site is
http://ghostbusters.cc
. There are hundreds of similar organizations that can be found on the Internet that provide resilience services or continuity of operations for crimeware support infrastructures.
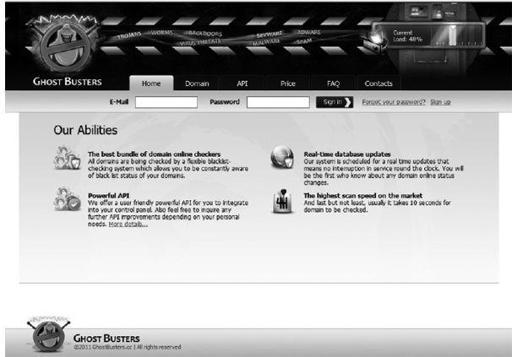
Ghost Busters domain status notification service
Ghost Busters domain status notification service pricing
When sending URLs to colleagues or peers, it is recommended you employ a commonly used method in the security community known as “hxxp,” which ensures your browser does not accidently go to or visit an IP address, domain, or site that is under investigation or of interest (for example,
hxxp://ghostbusters.cc
).
In the Ghost Busters example, you can even see their current load (which means you’re busy reading this book and not stopping the bad guys), which is 48 percent (almost half capacity), which means they are not that busy processing notifications or analyzing blacklists. The load on this site goes up when more customers are being notified in large volumes or there are new public blacklists being analyzed, which will be followed by notifications to customers. We have seen this load as high as 64 percent (which means the good guys were busy; keep reading and learn).
As you can see, this is a legitimate service that provides customers with notifications when one of the domains in their account list ends up on a public or other blacklist. Any member can have a list of domains, which is not a crime, and there is little guilt by association on the anonymous Internet.
You will find this service, and several others like it, recommended on numerous underground forums. Although it is a legitimate service, it can also help criminals efficiently maintain their command-and-control structure without outages or downtime (which means loss of revenue). You can see the services they offer could come in very handy for a criminal or state-sponsored cyber threat:
The best bundle of domain online checkers—increases attacker agility
Real-time database updates—for organized and motivated operations
Powerful APIs—for control panels