Reverse Deception: Organized Cyber Threat Counter-Exploitation (61 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

Underground forum discussion regarding a specific ripper from “Ghana”
Now what about if someone does not like another member and generates data to file a false complaint to ruin another’s reputation? It has happened, but not that often, since most of the time, the reviewers are peers or colleagues who have the intellect and savvy to identify if a false allegation is legitimate. If an allegation is falsified and someone is found guilty of lying, that is one of the worst things you can do as a member of one of these communities. This type of person becomes ostracized even more. This puts an individual in a bad place when his target markets are others within the community.
Injection Vectors
We’ve already talked about injection vectors, but we want you to read this from a different perspective—from the view of a proactive threat intelligence analyst. Whether you are the target of an SSCT or an opportunistic criminal, these methods are used as injection points into your enterprise.
Why would targeted threats use their “ace in the hole” (author coughs loudly and murmurs something that sounds like “Stuxnet”)? There will always be the initial use of tools, techniques, and vehicles that are found on sites similar to the ones mentioned in this book. Almost anything security professionals want to learn about their adversaries is right there in plain sight for everyone on the Internet (as long as you take the time to follow the chatter).
Social Engineering
Social engineering is by far the single most powerful injection vector for malware writers. It’s based on the inability of trusted insiders to recognize that they are reading a generic “dancing bear” e-mail or a highly sophisticated and targeted e-mail. Both forms are designed to fool the reader into opening or executing the content and/or attachment in order to take control of the recipient’s system.
E-mail as a Malware Backdoor
A newer injection vector first seen in the summer of 2008 is malware that is intelligent enough to download its own Secure Socket Layer (SSL) dynamic link libraries (ssl.dll files). The malware with this unique capabilities is shown as custom or tailored and more advanced than most of the commercially available criminal tools that can open its own hidden covert channel to external public web mail systems (such as Yahoo!, Hotmail, and Gmail). What does that mean for you? It means communications from your internal systems heading to public personal e-mail systems could be malware logging in to receive new updates or instructions, or it could be sending out data from your internal network.
The use of SSL or encrypted channels over port 443 (SSL) is becoming more common practice among most of the “do-it-yourself” crimeware kits as an add-on or plug-in that costs additional money for the capability. This has been spotted several times in the United States by several clients, ranging through different sectors of industries. More important, these customers are large international conglomerates with billions at stake and have no defense against an internal host using port 443 as a point of cover communications. This is why analysis of the size, time of transmission, source, and destination (IP address or domain in a country of interest) should be used as a method for identifying possible SSL-based unauthorized communications in and out of your enterprise as a part of your overall investigation into a threat.
Phishing
Phishing currently has the attention of anyone working in any IT-related industry. One of your users at work or at home gets an e-mail that seems legitimate but is actually a cleverly crafted façade to lure an end user into clicking a link or providing personal or professional information. This can lead to enough information disclosure to steal the identity of that person. It also could be used to gather enough information from that person to get more information on that person’s corporation. This information could allow threats to gain access to private or public information resources to cause more damage or to make a profit.
Exploit Packs
The following is a short list of some of the most commonly seen criminally maintained exploit kits (EK) available for use on the underground market today.
| EK Pack | First Mentioned |
|---|---|
| NeoSploit EK | 2007 |
| Phoenix EK | 2008 |
| Eleonore EK | 2009 |
| CrimePack EK | 2009 |
| Fragus EK | 2009 |
| Siberia EK | 2009 |
| Yes Exploit | 2009 |
| El Fiesta EK | 2009 |
| JustExploitIT | 2009 |
| ICEPack EK | 2009 |
| Mpack EK | 2009 |
| Web Attacker | 2009 |
| Tornado EK | 2009 |
| Incognito EK | 2010 |
| Zombie EK | 2010 |
| Blackhole EK | 2010 |
| Bleeding Life | 2010 |
All of these criminally maintained packages reside on a server of the operator’s design. They are either visited via obfuscated redirects (you visit one site and are automatically forwarded to another) or hacked websites with an exploit pack embedded within the site’s pages, which will attempt to exploit every visitor to that site. More often than not, you will find hacked websites with embedded redirects, as they are easier to hide from web administrators for longer periods, rather than those that upload the entire pack to a hacked web server. Overall, all of these exploit packs contain various browser- and application-based exploits, which once downloaded by the victim, will execute and then perform the desired action of the distribution provider. This is typically the pushing of a downloader or dropper onto the victim’s machine, where that initial binary unpacks its own packaged tools (dropper) or downloads additional components from one or more domains or IP addresses (downloader).
Here is a short list of some of the exploits that some of the more prominent exploit packs have used. You will notice some of these exploits data back to 2003, which is a good reason to keep your systems as up to date as possible. This list is compiled of all mentioned exploit packs and also a few that are just being discovered by the security community in Q2 2012.
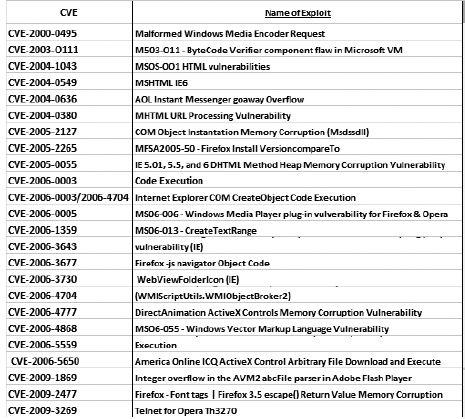
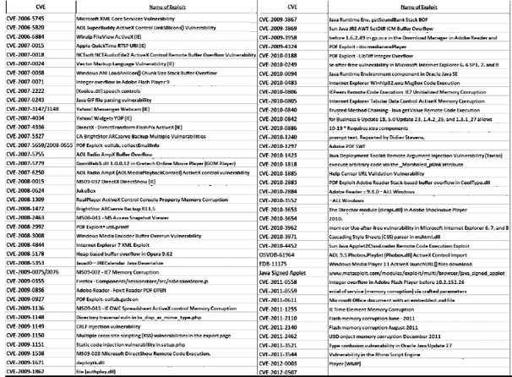
List of current CVEs used by modern (5/2012) exploit kits
Although no single exploit pack has a comprehensive set of all exploits, the distribution providers are becoming more agile and including more and more exploits in their kits. This is one of the primary reasons so many of the larger criminal organizations have been leveraging these distribution providers more frequently. Here are a couple screenshots of some of the more prominent exploit packs seen over the years.
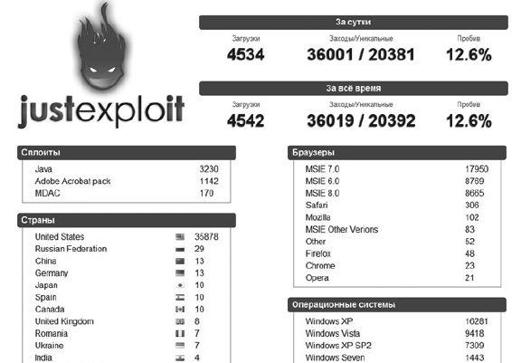
JustExploit exploit pack control panel
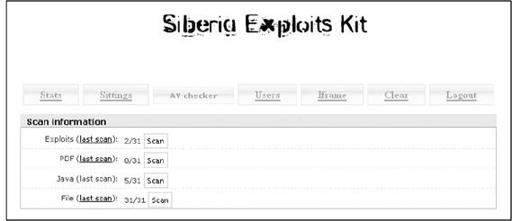
Siberia exploit pack control panel
As you can see, each of these exploit packs has a list of client-based exploits that can target a victim’s system upon visiting a specific website or URL. The site doesn’t even need to completely load; just identifying the victim’s system and browser type will generally be enough to launch a client-side exploit against a victim.
The same tools that are in use by opportunistic criminals are also employed by motivated and well-funded adversaries. The reasons are simple: they are inexpensive, they are difficult to attribute among all the other similar families of tools being used, and volumes of information can be stolen. It is very easy for attackers to set up their own criminal infrastructure. It can take less than a $3,000 investment, and within a year, the criminals make their first $3 to $6 million. Both numbers are drops in the bucket to world governments with intelligence and espionage collection objectives.

Conclusion
In this chapter, you learned about the breakdown of some of the latest tactics, tools, and methods of cyber criminals. You should realize that there is way too much out there today for any single professional to tackle alone. This is why it is important to have a team composed of specialists in varying areas, such as incident handling, digital forensic analysis, and intelligence analysis. Being able to analyze the tools and techniques used during an intrusion is important to better understand the who and why behind the breach of your enterprise.
CHAPTER
7
