Reverse Deception: Organized Cyber Threat Counter-Exploitation (56 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

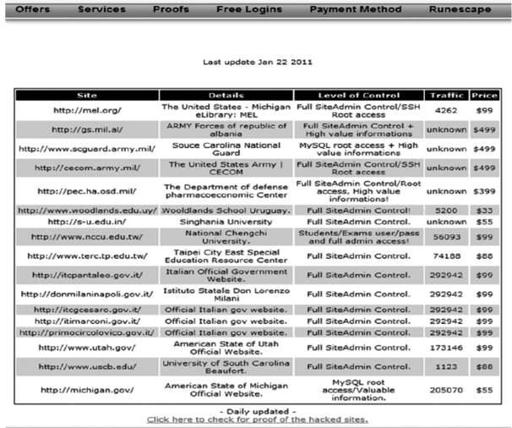
Targeted subleasing of specific high-value systems
There are several more pages on this site, with more accounts posted for sale. The operator would even validate the p0wnage of these systems by using a freeware product called TeamViewer—nifty, and actually comparable to window shopping. The site also shows the volumes of traffic to that site to illustrate potential infections possible to the third party from users of the compromised server. This information is collected by having control of the server and logging the traffic that hits that server or system on a daily basis (very thoughtful).
Opportunistic Attacks
Most of the time, your enterprise is compromised by an opportunistic threat that is essentially operated and maintained by a distribution provider (infector group). This type of group will run multiple campaigns at once, as the participants are under contract or agreement to infect a certain number of hosts per day, week, or month.
This type of campaign or operation isn’t specifically targeting your enterprise. The goal is simply to infect as many systems as possible, and systems within your enterprise ended up being a part of this infection campaign. Some groups do not pay any attention to the end victim’s network association and perform the infections for monetary gain.
The following is an example of an affiliate website discovered in March 2011 that lets visitors register as distribution provider (infector) affiliates and offers a malicious loader (a small Trojan that can download additional malware) that you can use in your infection campaign. Once that loader is pushed on to a victim and executed, it phones back to the operations team. As you can see, the group claims “We pay for all installs!”

TDL affiliate group, Gangsta Bucks
NOTE
The Gangsta Bucks group is an affiliate of the TDL Gang (aka the Tyler Durden Loader Group), the most wanted and illusive cyber-criminal development team in the world. This group stayed in the top-ten largest criminal infrastructures (botnets) throughout all of 2010. There has been a lot of research done in the world on the TDL Gang, and many groups in the white hat community have been working together to attribute this gang’s malware to the handful of folks behind the development of the rootkit (we know who two of you are)
. Spasibo
for all of the help you have done leaving trails and crumbs in your code and in your affiliate networks
.
Within each loader is a specific ID tied to the infector’s ID or account. The group is paid per 1,000 system infections in US dollars (which is a lot of money in countries where cyber crime is an accepted occupation). As you can see in the following screenshot, there is a sliding scale of rates based on infections per country. The United States is the most lucrative. Other countries that have large economies are of high value, and countries with secondary and tertiary economies are also on the list.

TDL affiliate (infector) pricing for pay-per-install third parties pay scale
Most groups who focus on the quick-and-easy way to riches don’t monitor their victims. They simply sell the access to their victims’ resources for gain, and then from there continue on to another campaign. Almost all criminals pay a good deal of attention to the end victims and generally attempt to sublease their victim systems to the highest bidder. Sometimes they will even sublease to more than one other criminal group in order to make more money, which means the information stored on the infected system can be accessed by more than one criminal gang.
Numerous groups sublease or coordinate activities in order to make the most money for their effort. This has become common over the past few years.
Opportunistic Subleasing
Third parties are sold victim systems in volume by the operators of affiliate sites like Gangsta Bucks. There are numerous underground forums, IRC, Jabber, and other locations in the depths of the Internet where access to compromised systems is actively bought and sold to the highest bidder. These systems are generally subleased by country, but are also sold by type of industry, a specific company, or by corporate roles (C-level accounts, for example). These are almost always sold off in bulk, either for a period of time or permanently, the latter being the most expensive. The following are some examples of websites or postings of services being subleased by opportunistic criminal operators.
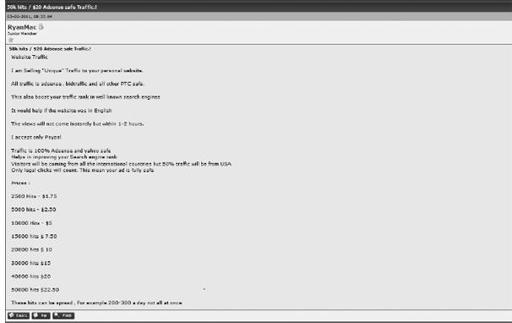
Underground forum post selling traffic to your website or web server
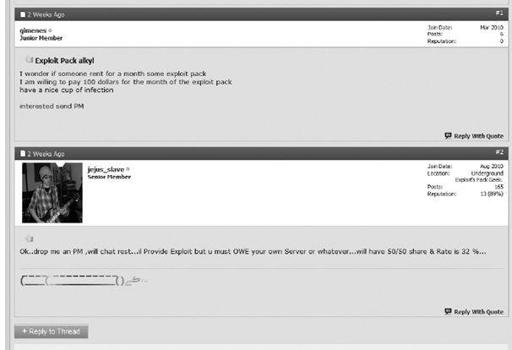
Underground forum post requesting the lease of an exploit kit
These images show that criminals actively sell off portions of their criminal infrastructure to third parties who are either opportunistic or targeted-based attackers, whose true motive/intent is of no consequence to the initial seller of these resources.
Opportunistic Usage
The group who posted the following advertisement was offering targeted attacks from volumes of systems that were more than likely gained through the use of opportunistic infection campaigns.
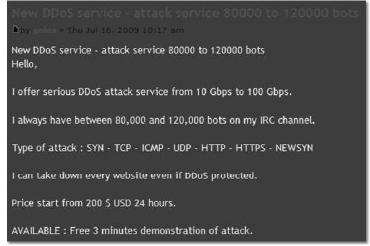
Underground forum posting offering opportunistic-based DDOS services
The services they were offering (and maybe still are) were targeted based on their customer’s requests. However, the use of the systems is opportunistic for the operator and not the customer. This is one of the ways in which opportunistic cyber crime can become targeted very quickly. Hundreds of similar groups are selling services for monetary gain from opportunistic infections. These groups should be taken as seriously as those who perpetuate targeted attacks, as they can quickly turn your enterprise into a component of a weapon for a targeted attack.
It is difficult to determine if an incident was targeted or opportunistic, which is why the analysis of observables of any incident is so important. The observables can supply professional analysts with the knowledge to assess whether the attack was targeted or opportunistic.
Opportunistic Turning Targeted
Some criminal operators take the time to identify each specific enterprise of their victims, and then break their large campaign into pieces and sell them off in large, small, and one-off sections part by part. This requires a lot of analysis on the end of the operators of the criminal infrastructure, but typically yields the highest return on investment (ROI). That’s right, even the bad guys expect an ROI, especially organized criminal gangs.
Almost every organized crime ring in any country operates at a level and boundary outside its government’s law in and outside its country. That being said, you can imagine some of the things an intelligence agency could push an organized crime group to carry out in return for turning a blind eye to certain criminal operations. The governments and law enforcement agencies of Russia, China, and many other countries may allow nefarious activity to continue, as the opportunistic criminals know who to call on a short list when something juicy pops up on the radar.
