The Dawn of Innovation (46 page)
Read The Dawn of Innovation Online
Authors: Charles R. Morris

A country's international credit/debtor position is the difference between all American claims on the rest of the world and vice versa. Foreign claims on America include not only outright borrowings, but any foreign ownership of stock, land, or any other American asset. The United States was a net debtor nation through the entire nineteenth century, primarily because of foreign investment flows, as in the late 1830s, 1850s, and post-Civil War booms in railroads, cattle ranches, and other real assets. America first became a net overseas investor in the late 1890s, mostly in Canada and Latin America. The huge surpluses earned during WWI made the United States by far the world's largest creditor nation.
24
24
And now, as everyone knows, America is itself in danger of being pushed off the top-dog pedestal. In the next chapter we will look briefly at the looming contest for economic dominance between China and the United States, and its similarities and differences compared with the one between Great Britain and America a century and a half ago.
CHAPTER NINE
Catching Up to the Hyperpower
A Reprise?

T
HE RAPID GROWTH OF THE CHINESE ECONOMY IS ONE OF THE MOST portentous phenomena in the world today.
1
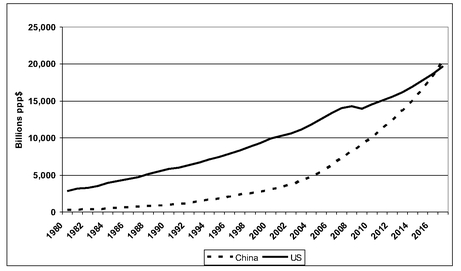
Chart 9.1 shows the data comparing the total economic output of China and the United States from 1980 through 2011, and projected through 2017, as compiled by the International Monetary Fund (IMF).
HE RAPID GROWTH OF THE CHINESE ECONOMY IS ONE OF THE MOST portentous phenomena in the world today.
1
Chart 9.1 shows the data comparing the total economic output of China and the United States from 1980 through 2011, and projected through 2017, as compiled by the International Monetary Fund (IMF).
Some comments on the data. The comparison is measured in “purchasing power parity” dollars (ppp$). Official dollar/RMB exchange rates do not fully capture the pricing differences between China and the United States, especially in labor-intensive services, which are typically very cheap in a low-wage country. Using ppp$ inflates Chinese output by about 50 percent over currency market values. No one would claim that ppp calculations are accurate, but most analysts accept that they provide a better fit to reality. Projecting economic growth based on official currency rates tends to show that it will take well into the 2030s before Chinese GDP catches up with America's. All such comparisons, however they are adjusted, are only gross approximations of reality, given the radical differences between the two economies. Even taking the IMF forecasts at face value, China will hardly be a rich country in 2017, since it will be distributing approximately the same purchasing power as the United States among four times as many people.
Â
CHART 9.1 Chinese and US GDP ppp$: 1980â2017 (est)
SOURCE:
World Economic Outlook,
International Monetary Fund, April 2012.
World Economic Outlook,
International Monetary Fund, April 2012.
China's rapid growth, however, is already triggering another crucial process, Michael Spence's middle-income transition, introduced in the last chapter. About the point at which per capita incomes rise to between $5,000 and $10,000, a broader middle class begins to take control of its future and define the tone of economic life. Since self-directed people are often unwilling to accede to petty officialdom in matters they deem important, the transition can be particularly treacherous in a state-driven economy like China's.
2
2
We will come back to that point, but first we will look at some of the broad similarities between America's tactics against Great Britain in the nineteenth century and China's catch-up strategies today.
The Pleasures of Starting in Second PlaceTHE JOY OF THEFT
The United States had a fine record of innovation from its earliest post-colonial days, but its inventiveness was mostly lavished on large-scale production and distribution techniques for established products. The nineteenth century's iron and steel technologyâthe blast furnace, Bessemer conversion, the “basic” process, the Siemens open-hearth furnace, the cast steel of Sheffieldânearly all came from Great Britain, with some important but lesser contributions from France and elsewhere on the continent. Roughly the same could be said of textile technology, coal and coke, steam engines, chemicals, and precision machinery. Britain's policy was to keep such technologies out of the hands of its North American colonies, which were supposed to serve as the rural hinterland of industrializing England, supplying scarce timber, grains, and ores and providing a captive market for home-country manufactures.
But once independent and determined to industrialize on their own, Americans saw this immense hoard of technology as theirs for the askingâor for the stealing. Tench Coxe was Alexander Hamilton's deputy in the first Treasury Department, and he had no compunction about offering cash awards for stolen British textile technology and paying bounties high enough to induce craftsmen to risk prison for emigrating with trade secrets. Americans viewed Great Britain as a semihostile power, and understood that their own poorly diversified economy was a source of vulnerability. Conventional ethics do not apply in the game of nations, and the United States set out to steal whatever it could. Knowledgeable Chinese occasionally cite that history when they are criticized for their disregard of intellectual property rules.
Japan adopted a similar strategy vis-Ã -vis the United States in the postâWorld War II era, even though it was among America's closest allies. Companies like Cummins Engine subcontracted production to companies
like Komatsu in the 1960s to take advantage of Japan's low labor costs. Within a few years, Cummins's home diesel market was attacked by inexpensive but disconcertingly high-quality Cummins knockoffs from Komatsu.
like Komatsu in the 1960s to take advantage of Japan's low labor costs. Within a few years, Cummins's home diesel market was attacked by inexpensive but disconcertingly high-quality Cummins knockoffs from Komatsu.
China's relationship with America is much like that of the fledgling United States with Great Britain. China is both the United States' second largest trading partner (after Canada) and an avowed rival. The American navy is an intrusive presence close to its shores, and smaller countries that it views as within its sphere of influence pointedly take shelter in America's shadow. Relations have an extra edge because the United States stands for the kind of raucous, self-indulgent democracy that China's leaders fear could destabilize their own fragile ruling compact. So with respect to technology, much as America did, China is stealing all it can, not only from the United States but from all Western advanced economies.
A recent roundup by
Businessweek
listed nineteen recent convictions under American economic espionage laws for intellectual property theft by Chinese agents and company moles. The roster of victims reads like a Who's Who of corporate America: Apple, Boeing, Chicago Mercantile Exchange, Dow Chemical, DuPont, Ford, General Motors, Goodyear, Motorola, Northrup Grumman, Sanofi-Aventis. The targets ranged from formulas for industrial fireproof paint to detailed specifications for the space shuttle and a wide range of military aircraft; from derivative trading software and algorithms to polyethylene shielding; from titanium pigments to trash management software; from advanced display technology to automobile design specifications and advanced wind turbine management software. Some of the evidence included records of government officials supplying shopping lists and offering encouragement.
3
Businessweek
listed nineteen recent convictions under American economic espionage laws for intellectual property theft by Chinese agents and company moles. The roster of victims reads like a Who's Who of corporate America: Apple, Boeing, Chicago Mercantile Exchange, Dow Chemical, DuPont, Ford, General Motors, Goodyear, Motorola, Northrup Grumman, Sanofi-Aventis. The targets ranged from formulas for industrial fireproof paint to detailed specifications for the space shuttle and a wide range of military aircraft; from derivative trading software and algorithms to polyethylene shielding; from titanium pigments to trash management software; from advanced display technology to automobile design specifications and advanced wind turbine management software. Some of the evidence included records of government officials supplying shopping lists and offering encouragement.
3
All of those cases involved Chinese agents on site in the target companies, often in responsible positions, physically stealing or copying sensitive material. Far more widespread, most experts agree, are cyber-invasions by government-sponsored or protected hackers. For nearly a decade, Chinese hackers thoroughly compromised the data systems of the erstwhile Canadian telecommunications giant Nortel, seizing more or less complete access
to all of the company's product designs and other trade secrets. Disquietingly, there is a distinct possibility that after Nortel was broken up and sold in bankruptcy to several other technology companies, the infections were transmitted to the new hosts.
4
to all of the company's product designs and other trade secrets. Disquietingly, there is a distinct possibility that after Nortel was broken up and sold in bankruptcy to several other technology companies, the infections were transmitted to the new hosts.
4
Data from the US Cyber Command in the Department of Defense tabulate more than 50,000 malicious cyber-intrusions per year in recent years. It does not break out the data by country of origin, but China is clearly a major contributor. In 2011, for example, RSA, a leading vendor of security technology for corporate data systems, was itself hacked into. Subsequent analysis showed it be an extremely sophisticated attack, dubbed an “Advanced Persistent Threat.” Although it had been routed through several countries and continents, the attack appeared to emanate from China. One apparent object of the attack was to compromise the security-key systems for accessing confidential company databases, possibly including those of RSA's customers. If it had been successfulâthe company said it was “confident” that it had not been, but who knows?âit would have operated as an open sesame to acres of sensitive, and highly valuable, material.
5
EXPLOITING PARTNERS5
In the early days of independence, the United States was almost entirely dependent on Great Britain for manufactured products beyond the capabilities of local seamstresses and blacksmiths. British products were consigned to coastal merchant houses that distributed them throughout the country. Typically, it was those merchants who provided the capital for local artisans to create knockoffs of the British designs and keep the profits at home.
The Chinese behave the same way. But since today's high-value products are often far too complex to readily knock off, they exploit the eagerness of Western companies to gain entry to the vast potential Chinese market. Recently GE, anxious to land a large avionics contract (flight management software and technology) for a projected Chinese jumbo commercial jet, agreed to transfer technology developed for the Boeing 787 Dreamliner
to a fifty-fifty joint venture in Shanghai. Since the technology has obvious military applications, GE says that Chinese military personnel will be excluded from the joint venture and that there will be limits on exâproject employees transferring to Chinese military programsâprotections that one congressman called “laughable.”
to a fifty-fifty joint venture in Shanghai. Since the technology has obvious military applications, GE says that Chinese military personnel will be excluded from the joint venture and that there will be limits on exâproject employees transferring to Chinese military programsâprotections that one congressman called “laughable.”
GE stresses that the deal was vetted by both the Commerce and Defense Departments. But a deal valued at $300 million and creating at least a few hundred jobs in the United States, but many more in China, was hardly likely to be turned down in the midst of a “jobless recovery.” Four other aviation technology companies will also benefit from the contracts, and for GE, the deal came bundled with the promise of additional deals in coal gasification, energy, locomotives, and a high-speed-rail joint venture that could be worth another $1 billion.
6
Imagine the row GE would have kicked up if the deal had been turned down.
bu
6
Imagine the row GE would have kicked up if the deal had been turned down.
bu
If the past is portent, the likelihood of the joint venture working out well for GE is not high. Siemens and ThyssenKrupp worked closely with a Chinese high-speed-rail consortium supplying maglev technology to its Shanghai bullet trains. China is now proceeding with maglev development elsewhere in the country without the German partners, and it may soon be competing with them for global sales. That same prospect is looming in a number of other industriesâsolar power, batteries, aviation, automobiles, chemical manufactureâin which Germany has supplied advanced technologies to Chinese customers and partners.
7
7
Incidents like these are not random occurrences, the kind of occasional flaps that are inevitable when two companies with different cultures and languages engage as close partners in complex undertakings. Ever since the end of the Maoist Cultural Revolution, China has made no secret of
its intent to move rapidly up the technology ladder by virtually any means, fair or foul. Specific plans offered as part of the regular five-year national planning cycle emphasize “indigenous innovation,” which is defined to include “enhancing original innovation through co-innovation and re-innovation based on the assimilation of imported technologies,” and states that “the importation of technologies without emphasizing the assimilation, absorption and re-innovation is bound to weaken the nation's indigenous research and development capacity.” The US Chamber of Commerce said that the technology plans taken together amounted to “a blueprint for technology theft on a scale the world has never seen before.”
8
its intent to move rapidly up the technology ladder by virtually any means, fair or foul. Specific plans offered as part of the regular five-year national planning cycle emphasize “indigenous innovation,” which is defined to include “enhancing original innovation through co-innovation and re-innovation based on the assimilation of imported technologies,” and states that “the importation of technologies without emphasizing the assimilation, absorption and re-innovation is bound to weaken the nation's indigenous research and development capacity.” The US Chamber of Commerce said that the technology plans taken together amounted to “a blueprint for technology theft on a scale the world has never seen before.”
8
Other books
The Zen Gene by Mains, Laurie
This Case Is Gonna Kill Me by Phillipa Bornikova
Strange Mammals by Jason Erik Lundberg
Stagecoach by Bonnie Bryant
A Necessary End by Peter Robinson
Hearts Ablaze (Hearts On Fire Series) by Heather Lyn
Surrender My Love by Eugene, Lisa
Mine: Black Sparks MC by Glass, Evelyn
The Box of Delights by Masefield, John