Reverse Deception: Organized Cyber Threat Counter-Exploitation (16 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

Skills and methods
The tools and techniques used throughout the event
Actions
The precise actions of a threat or numerous threats
Attack origination points
The number of points where the event originated
Numbers involved in the attack
How many internal and external systems were involved in the event, and how many people’s systems have different influence/importance weights
Knowledge source
The ability to discern any information regarding any of the specific threats through online information gathering (you might be surprised by what you can find by being a little
proactive
)
Let’s talk about these nine primary points of observation, or
observables
, from a counterintelligence perspective. These observables can more often be discerned from
each and every
intrusion or threat that comes across the wire and enters a portion of the enterprise or systems you control. In a sense, they are a way of looking at all of the information you have at hand from a step-back approach that enables you to see things a little more clearly.
Most organizations look at events after they have occurred, or “postmortem,” so the reactive mode repeatedly occurs after an intrusion has been detected by security professionals. Dealing with intrusions, whether advanced or persistent, can be highly difficult when simply focusing your operations on a reactive model. The following diagram breaks down what we have observed over the years. This diagram does not cover every organization, but it does illustrate the overall victim’s perceptions when handling a threat postmortem based on our professional experiences.
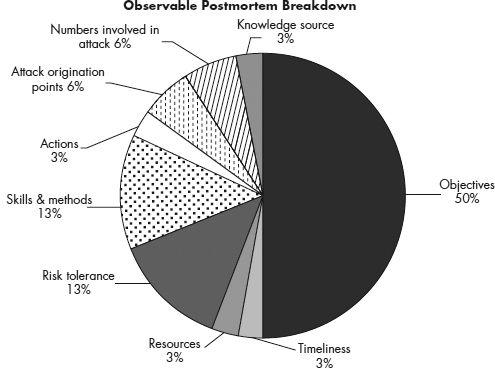
As you can see, the most perceived observable is the objectives of the threat. What was stolen, taken, or modified is commonly perceived as the end goal. However, the totality of the breach needs to be measured in order to attempt to understand the end game of the adversary or attacker. By the time a security team responds to an attack after it occurs, the other pieces of the puzzle can become more convoluted and difficult to discern. Logs get lengthy, tools are disabled, and patterns are not recognized in time to understand the other observable details a threat can leave. These details are like a trail of bread crumbs. The observables can be combined into a concise report of the attacker’s overall motives and intent.
All too often, stakeholders are concerned with simple remediation and cleanup after the fact, and then business goes back to usual. One of the major issues with this model is always being in reactive mode. You are not looking at what’s going on currently and what may be coming in the future. Always reacting to intrusions costs you nothing but headaches and money. Most organizations will simply rebuild a hard drive prior to examining the evidence on the host system.
The waiting is the most painful part for most security professionals—waiting for the proverbial other shoe to drop. An intrusion is going to happen—it is just a matter of time. So let’s start talking about being proactive and establishing a model that provides the security professional a better understanding of the state of threats, adversaries, and intrusions.
To be proactive, you employ tools and tactics within your operational boundaries that increase your ability to detect, identify, track, and counter PTs and APTs. There are tools and methods available both commercially and publicly (which does not necessarily mean free) that combined can assist a security professional in establishing a definitive list of observable traits of a threat. The following is a chart that we use when working with customers to define the value added to a security program with our recommended tools and tactics.
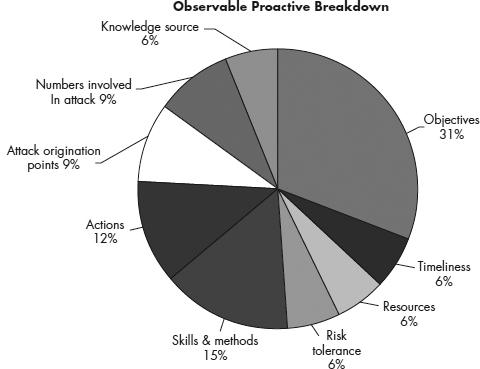
As you can see, there is a significant difference between the postmortem and proactive breakdowns in the two pie charts shown here. These charts are based on solved cases where attribution via intrusions was successful and led either to the identification or apprehension of the individual or group behind the threat. Although charges may not have been brought against the perpetrators, intelligence dossiers have been built and are being maintained by intelligence and law enforcement agencies around the world.
Now when looking at the analysis breakdown after each example of the overall approach to adversary analysis, you should see that we are drilling down on more than one observable that most professionals are generally unable to quantify when operating in a postmortem or reactive model. Please understand even when being proactive and actively countering your threats and adversaries, you will eventually get hit by something or someone out of the blue and end up in postmortem mode. However, by reading this book thoroughly, when these moments do occur, you, your team, and your staff will be more prepared and empowered with the tools and tactics to counter advanced and persistent threats.

Examples of Advanced and Persistent Threats
In order to convey the severity of advanced and persistent threats, we’ll take a look at some of the more prominent ones that have made it into the public eye over the past several years. We will walk through each one, and introduce some concepts and principles that are core to identifying what type or level of threat you are up against. As you read earlier, you can generally relate an APT to a highly funded and backed organization, which is just as likely to be found in a PT. It is simply a matter of attributing the who, what, when, where, and why behind each intrusion.
Sometimes, the only way to understand a threat is to have it placed right in front of you for all the world to see. The lengths, depths, and brass balls of some of these examples—from not only an advanced perspective but also a highly persistent perspective—may not blow your mind, but will certainly raise your blood pressure.
As we revisit and briefly examine some of the more mentioned APTs that have been publicly disclosed, we will not get into the politics of it all, point fingers, or divulge any information that is not publicly available or has not been previously mentioned in public forums. We will simply look at what has been publicly disclosed and the information about these events in order to introduce, illustrate, and convey why it is important to identify advanced and persistent threats as soon as possible. We will also show the nine observable points mentioned earlier in this chapter for each threat.