Reverse Deception: Organized Cyber Threat Counter-Exploitation (78 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

EnCase
CWSandbox
IDA Pro
These are some open source/free analysis tools:
VirusTotal (site)
Forensic Toolkit (FTK)
Md5sum
Wireshark
These lists are not comprehensive. Many comparable tools are available and useful for analyzing production-based honeynets.
Data Collection
The data collection component applies primarily to organizations that implement multiple honeynets that are centrally managed by a honeynet management server. Typically, the architecture will have numerous honeywalls (roo) reporting to a honeywall manager (kanga). Roo is the name for the third-generation honeywall, and kanga is the name of the honeywall manager server for enterprise ready and highly distributed honeynets. The honeywall itself collects data for the honeynet and sends it to a kanga, which can manage more than 100 roos. This theme was borrowed by the Honeynet Project.
Generally, most organizations simply deploy a single instance of a honeynet. However, larger enterprises sometimes require multiple honeynets with various locations and types to fully understand a network’s true defensive posture. Distributed honeynets, where all data is centrally stored and correlated for the purpose of network defense or counterintelligence purposes, also fall into this category.
To date, the open source Honeynet Project has not released any stable or scalable enterprise sensor to manager builds. Savid Corporation is the only firm in the United States that provides US government-certified honeynet solutions that are custom and focus on the niche requirements of implementing enterprise honeynets.
Figure 8-3
shows a simple diagram of a data collection architecture that is commonly used by production-based honeynet implementations.
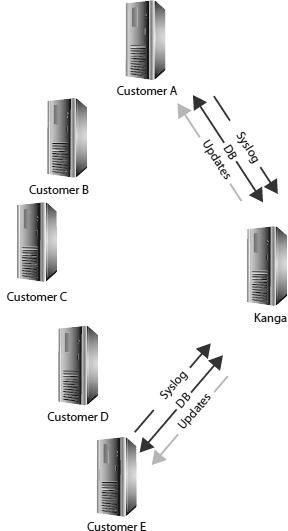
Figure 8-3
Generic data collection
Although they are more commonly found in larger enterprises, data collection methods are still applicable to single honeynet deployments where the management channel (eth2) of the honeywall requires the secure transfer between the honeywall and the actual systems where data is managed and analyzed. The following could be used as a simple approach to configure the basic open source honeywall to ship data between a sensor and a manager:
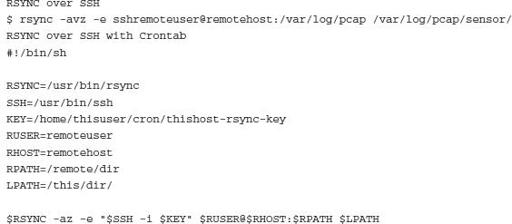
Honeynets as Part of Defense-in-Depth
The National Security Agency (NSA) generated a document titled
Global Information Grid Information Assurance Capability/Technology Roadmap
. This is meant to serve as a fundamental manual for implementing a complete defense-in-depth security architecture for any government organization operating and defending networks. On page 366 in Section 2.6.3.2, “Deception Technologies,” it clearly states that honeynet technologies are the only viable solution when attempting to quickly identify and acquire unauthorized or malicious activity within a government network.
This document contains more than 20 pages of material discussing honeynet technologies and their ability to dramatically augment and improve a network’s intrusion detection capabilities, while also providing security teams with the ability to quickly identify and act upon these unauthorized and/or malicious entities. This suite of technologies is accredited for NIPRNET and SIPRNET (names of the two major networks used by the US government cyber operations) use and has been researched as augmentations by various Department of Defense, Justice, and Energy organizations that are interested in learning more from cyber threats in order to enhance their network protection.
Research vs. Production Honeynets
In the early planning phases of a honeynet implementation, understanding what type your honeynet will be is critical. The two primary types of honeynets are research-based and production-based. The primary difference is in the goals of each type of honeynet. However, the following primary overall goals of honeynets are applicable to both types:
Fidelity in small data sets of high value
Reduction of false negatives