Alan Turing: The Enigma (51 page)
Read Alan Turing: The Enigma Online
Authors: Andrew Hodges
Tags: #Biography & Autobiography, #Science & Technology, #Computers, #History, #Mathematics, #History & Philosophy

Thus the summer of 1942 saw an unhappy state of affairs and highly frustrated young engineers. No use had been made of their electronics and Alan, who told them what was required, had not achieved anything either. It was a step in the right direction, but the Atlantic remained as opaque as it had become in February.
Hut 8, meanwhile, had acquired more high-level cryptanalytic staff, although the total never rose much above seven. At the end of 1941 Hugh Alexander had brought in Harry Golombek, the chess master, who also had returned from Argentina but had been obliged to serve two years in the infantry. Then in January 1942 arrived Peter Hilton, who had done just one term at Oxford reading mathematics and was only eighteen. He would describe his initiation thus:
43
… this man came over to speak to me and he said, ‘My name is Alan Turing. Are you interested in chess?’ And so I thought, ‘Now I am going to find out what it is all about!’ So I said, ‘Well, I am, as a matter of fact’. He said, Oh, that is very good, because I have a chess problem here I can’t solve.’
A whole day passed before Peter Hilton found out what he was there to do. But as 1942 went grimly on, this idiosyncratic style of organisation gave way to something more smoothly business-like. Alan remained ‘the Prof, but gently, subtly, Hugh Alexander became more and more the
de facto
head. In the nicest possible way, Alan found the rug being pulled from under his feet. He had brought the naval Enigma into being, but it needed a more adroit person to foster its development. He lacked the attention to detail, as well as other skills in managing people. Hugh Alexander was, for instance, the kind of person who could compose and write out a perfectly expressed memorandum without a single crossing-out – not at all a Turing strength. Inevitably Alan felt the loss, as one whose baby had been taken away. But he could not have disputed that Alexander was the better organiser, even though this upset the more cosy arrangements of 1941. Jack Good noticed
44
… one example of Hugh Alexander’s technique as an administrator. Since the section worked 24 hours a day, we had a three-shift system, so the ‘girls’ had three shift-heads. One of them made herself unpopular because she was always getting in a flap, although she behaved well in ordinary social relationships. Hugh said he’d like to experiment with a complicated five-shift system, so two new shift-heads were required. After a few weeks he decided that the experiment had failed,
and he returned to the three-shift system. Two of the shift-heads had to be dropped and you can guess who one of them was.
Alan would never have dreamt of so devious a ploy, although he would have laughed loudly enough when it was explained to him. He had in fact been quite helpful to the ‘girls’, in matters of leave and working hours, in the old 1940 days. But now a more professional approach to management was required.
Gradually he was being eased out of the immediate problems, and into longer-term research. It was personally disappointing, for he had enjoyed the shift work as much as any of them, and loved having the feel of the whole thing from beginning to end of the process. But it was a rational way of using his abstract mind. Though technically still attached to Hut 8, he now worked in a room of his own, becoming in effect the chief consultant to GC and CS. While the others worked on a ‘need to know’ system, not allowed to know anything beyond the specific sphere in which they were engaged, his role became unlimited. The Prof was let into everything, drawn deeper and deeper into the enormously expanded communications that now reflected a world in total war. It was not the same any more, but he could not complain. There was a war on, and he had a unique ability to put his country in the picture.
There was one picture emerging in fragmented form which was nearly as exciting as that of the Atlantic U-boats. The analysts had begun to intercept a small amount of traffic which was entirely different in character from the Enigma signals. It was not in Morse code, having instead the features of a teleprinter signal. Teleprinter transmissions, which had rapidly developed during the 1930s, employed the Baudot-Murray code, not Morse code, the point being that this was a system whose operation could be made automatic. The Baudot-Murray code represented letters of the alphabet by using the thirty-two different possibilities offered by five-hole paper tape. A teleprinter could translate the resulting pattern of holes directly into pulses; at the receiving end the pulses could be translated back into a written message without human intervention. This idea had been developed in Germany to create cipher machine systems, in which encipherment, transmission and decipherment were made automatic – systems more convenient, and making much more effective use of contemporary technology, than the Enigma.
From a logical point of view, the ‘hole’ in the tape might as well be a 1, and the ‘no hole’ a 0. So the transmissions were in the form of five sequences of binary digits, 0s and 1s. It had long since occurred to cryptographers that the Baudot-Murray code could be used as the basis for an ‘adding on’ type of cipher. The principle was dignified with the name of the American inventor G.S. Vernam. In fact a Vernam cipher was based on the simplest possible kind of adding, since ‘modular’ addition with binary digits would use nothing but the rules shown in the figure.
The Relay Race
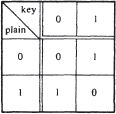
In other words, a plain-text teleprinter tape could be ‘added’ to a key teleprinter tape, according to the rule that a ‘hole’ in the key-tape would
change
the plain-text-tape (from ‘hole’ to ‘no hole’ or vice versa), while a ‘no hole’ would leave the plain-text unchanged,
*
as below.
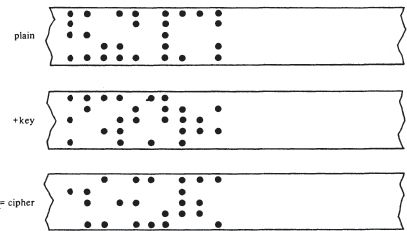
If the key were produced truly randomly, and used on the one-time principle, then such a system would be secure, the same for binary digits as for decimal digits. If all keys were equally likely, then no weight of evidence could accrue to any particular possible plain-text. But that was not the case with these German transmissions. The key was generated by the action of a machine. There were several different kinds of teleprinter-enciphering machines in use, but they shared common features, the key being a pattern generated by the irregular motion of ten or so wheels.
45
Such machines did not actually produce a paper key-tape, but from the cryptanalyst’s point of view it came to the same thing.
As with Enigma, there was always the possibility of an eventual hardware capture, and the German cryptographers should have allowed for that possibility. But the important break into this type of traffic did not, as it
happened, come about in this way. In 1941 someone at Bletchley guessed that a certain message had been sent out twice, and in a very particular way. Some fault in the system for using the machine had allowed an elementary blunder. The message had been sent out each time enciphered by the
same
key, but with the key advanced by one character in one transmission. Once this guess had been made, the recovery of both key and plain-text was a simple step.
With a machine designed for complete security, it should have proved impossible to make any further progress. The sequence of key thus elucidated should have appeared to be random, without any discernible pattern. But it was not. The decisive observation was made by W.T. Tutte, a young Cambridge chemist turned mathematician. This was the breakthrough equivalent to what the Poles had achieved with the Enigma in 1932. Like that work, it constituted a logical rather than a physical capture of the machine, and again it was only the very first step, the
sine qua non
. But one difference was that this time German industry had made a more serious effort. This was not a jumped-up version of a commercial device as was the Enigma. Another difference lay in its part in the German military system. This traffic was sparse but juicy, carrying high-level reports and appreciations. It brought Bletchley much closer to Berlin, at a time when Hitler was taking over personal direction of the war.
Even with an effective capture of the machine, further cryptanalysis should have been impossible: it was the rule of good cryptography. And the ‘period’ of the enciphering mechanism was not 17576 but a truly ‘tremendously large number’. Yet these problems proved not to be entirely insuperable, and by 1942 the analysts were beginning slowly to find ways to exploit the knowledge they had. The work on this particular type
*
of machine-enciphered traffic became known as
Fish
. One of the most important and general methods was developed by Alan on the basis of Tutte’s work in the course of his months of work during 1942 on Fish. It became known as ‘Turingismus’.
A new Bletchley industry was sprouting up. It was another way in which 1942 meant starting all over again from the beginning. But this was not to become Alan Turing’s game, as naval Enigma had been. For one thing, he had not been the one to start it off. For another, it was someone else who took the step of mechanising its analysis. This person was Newman, who arrived in summer 1942.
Newman had been recruited by his friend P.M.S. Blackett, the Cambridge physicist (and King’s College Fellow), who had been Professor of Physics at Manchester since 1937, and was currently applying statistical analysis to the problem of convoy organisation. (For at last the Admiralty was allowing scientific interference with its operations as well as with its intelligence.)
Newman was assigned to
the Research section to work on the Fish signals but found himself not particularly adept with the hand methods. He was thinking of going back to Cambridge, when he conceived of an approach that could be automated. The theoretical rationale was founded upon the statistical methods that Alan had developed during 1940 and 1941. These ideas, indeed, were crucial to Newman’s plans. But the implementation of them would require the construction of entirely new machines to do very fast counting operations. Newman persuaded Travis to approve this development, and the existing links with the Post Office Research Station were brought into play as early as autumn 1942. This recognition of their frustrated skills meant that the electronic engineers were able to make an impact after all. For the rest of 1942 the project was floundering on the engineering side, but this was not so much because of the electronics, as because of the mechanical difficulties associated with passing paper tape very rapidly through a reader.
Alan knew all about this project, but his active part in the Fish analysis was confined to ‘Turingismus’. This, in the autumn of 1942, was taken up by the section called the Testery,
*
where they tried out hand-methods on the Fish traffic – just as, years before, the Enigma decryption had painfully begun. Peter Hilton had been moved there from Hut 8, and then another arrival, in autumn 1942, was that of an even younger man, straight from Rugby School. This was Donald Michie, who had won an Oxford classics scholarship, and while waiting to do a Japanese course had entered elementary cryptological training. His talent recognised, he was thrust into the deep end at Bletchley. Both he and Peter Hilton developed Turingismus and reported their ideas back to its originator.
Although the news was so unremittingly bleak, and the prospects so uncertain, 1942 could be a wonderful, liberating year for the young, given opportunities and ideas that would never have been possible in peacetime. Alan’s own youthfulness much endeared him to the younger recruits. It was in fact his thirtieth birthday when the fall of Tobruk came as the latest in a series of disasters, but to those fresh from school it would be hard to decide whether one so ‘schoolboyish’ himself could be as much as thirty, or whether one carrying so much intellectual standing could be so young. A conversation with him was like being invited into some older boy’s study where House Colours and Chapel Parade gave way to illicit jazz and D.H. Lawrence novels, but where the housemaster had to turn a blind eye because a precious scholarship was being won.