The Code Book (58 page)

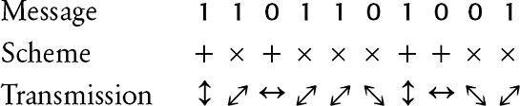
Alice transmits the first 1 using the +-scheme, and the second 1 using the ×-scheme. Hence, 1 is being transmitted in both cases, but it is represented by differently polarized photons each time.
If Eve wants to intercept this message, she needs to identify the polarization of each photon, just as the counterfeiter needs to identify the polarization of each photon in the dollar bill’s light traps. To measure the polarization of each photon Eve must decide how to orient her Polaroid filter as each one approaches. She cannot know for sure which scheme Alice will be using for each photon, so her choice of Polaroid filter will be haphazard and wrong half the time. Hence, she cannot have complete knowledge of the transmission.
An easier way to think of Eve’s dilemma is to pretend that she has two types of Polaroid detector at her disposal. The +-detector is capable of measuring horizontally and vertically polarized photons with perfect accuracy, but is not capable of measuring diagonally polarized photons with certainty, and merely misinterprets them as vertically or horizontally polarized photons. On the other hand, the ×-detector can measure diagonally polarized photons with perfect accuracy, but cannot measure horizontally and vertically polarized photons with certainty, misinterpreting them as diagonally polarized photons. For example, if she uses the ×-detector to measure the first photon, which is , she will misinterpret it as
, she will misinterpret it as or
or . If she misinterprets it as
. If she misinterprets it as , then she does not have a problem, because this also represents 1, but if she misinterprets it as
, then she does not have a problem, because this also represents 1, but if she misinterprets it as then she is in trouble, because this represents 0. To make matters worse for Eve, she only gets one chance to measure the photon accurately. A photon is indivisible, and so she cannot split it into two photons and measure it using both schemes.
then she is in trouble, because this represents 0. To make matters worse for Eve, she only gets one chance to measure the photon accurately. A photon is indivisible, and so she cannot split it into two photons and measure it using both schemes.
This system seems to have some pleasant features. Eve cannot be sure of accurately intercepting the encrypted message, so she has no hope of deciphering it. However, the system suffers from a severe and apparently insurmountable problem-Bob is in the same position as Eve, inasmuch as he has no way of knowing which polarization scheme Alice is using for each photon, so he too will misinterpret the message. The obvious solution to the problem is for Alice and Bob to agree on which polarization scheme they will use for each photon. For the example above, Alice and Bob would share a list, or key, that reads + × + × × × + + × ×. However, we are now back to the same old problem of key distribution-somehow Alice has to get the list of polarization schemes securely to Bob.
Of course, Alice could encrypt the list of schemes by employing a public key cipher such as RSA, and then transmit it to Bob. However, imagine that we are now in an era when RSA has been broken, perhaps following the development of powerful quantum computers. Bennett and Brassard’s system has to be self-sufficient and not rely on RSA. For months, Bennett and Brassard tried to think of a way around the key distribution problem. Then, in 1984, the two found themselves standing on the platform at Croton-Harmon station, near IBM’s Thomas J. Watson Laboratories. They were waiting for the train that would take Brassard back to Montreal, and passed the time by chatting about the trials and tribulations of Alice, Bob and Eve. Had the train arrived a few minutes early, they would have waved each other goodbye, having made no progress on the problem of key distribution. Instead, in a
eureka!
moment, they created quantum cryptography, the most secure form of cryptography ever devised.
Their recipe for quantum cryptography requires three preparatory stages. Although these stages do not involve sending an encrypted message, they do allow the secure exchange of a key which can later be used to encrypt a message.
Stage 1
. Alice begins by transmitting a random sequence of 1’s and 0’s (bits), using a random choice of rectilinear (horizontal and vertical) and diagonal polarization schemes.
Figure 76
shows such a sequence of photons on their way to Bob.
Stage 2
. Bob has to measure the polarization of these photons. Since he has no idea what polarization scheme Alice has used for each one, he randomly swaps between his +-detector and his ×-detector. Sometimes Bob picks the correct detector, and sometimes he picks the wrong one. If Bob uses the wrong detector he may well misinterpret Alice’s photon.
Table 27
covers all the possibilities. For example, in the top line, Alice uses the rectilinear scheme to send 1, and thus transmits ↕; then Bob uses the correct detector, so he detects ↕, and correctly notes down 1 as the first bit of the sequence. In the next line, Alice does the same thing, but Bob uses the incorrect detector, so he might detector
which means that he might correctly note down 1 or incorrectly note down 0.
Stage 3
. At this point, Alice has sent a series of 1’s and 0’s and Bob has detected some of them correctly and some of them incorrectly. To clarify the situation, Alice then telephones Bob on an ordinary insecure line, and tells Bob which polarization scheme she used for each photon-but not how she polarized each photon. So she might say that the first photon was sent using the rectilinear scheme, but she will not say whether she sentor
. Bob then tells Alice on which occasions he guessed the correct polarization scheme. On these occasions he definitely measured the correct polarization and correctly noted down 1 or 0. Finally, Alice and Bob ignore all the photons for which Bob used the wrong scheme, and concentrate only on those for which he guessed the right scheme. In effect, they have generated a new shorter sequence of bits, consisting only of Bob’s correct measurements. This whole stage is illustrated in the table at the bottom of
Figure 76
.