Reverse Deception: Organized Cyber Threat Counter-Exploitation (8 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

When to Deceive
The following is a simple diagram that attackers or defenders of networks may use to organize their thinking about deception. Clearly quite simple-minded, it is meant only to provoke. Also, it illustrates the need to think about attacking and attackers along a continuum—a fairly long one. This is also the case with deceptive defenses and defenders.
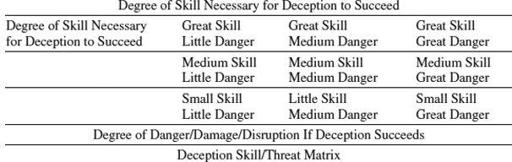
Deception originating in the lower-right corner of this diagram may be least dangerous to the defenders. At first glance, attacks originating in the upper-right corner might be considered most threatening. Defenders probably would be looking here. But the most dangerous attacks might come from the lower-right corner. It depends on how cleverly the adversary can conceal himself and the quality of the defender’s intelligence and analysis.
What is one to make of other parts of the matrix? Have attacks showing high levels of skill occurred, yet posed little danger? Why would a skillful attacker bother? Perhaps this is the exercise ground for high-competence organizations that want to train or experiment without rousing alarm?
From the deceiver’s point of view, the table may look very different. The deceiver’s aim is to induce behavior, not to reap immediate results. One objective might be to not alarm the defense so that attacks could be characterized by persistence at lower levels of threat. The hope would be to find exploitable points where exploitable behavior might be induced or where indications that the adversary was reacting as desired could be gathered. Perhaps the center row is where deceivers may be most populous. Here, the important distinction is between the hacker’s intent only on scoring status points or committing outright crimes on the one hand, and those attempting to manipulate the behavior of networks and their managers for ultimate ends on the other.
Contemplating the upper-right side of the table from the deceiver’s standpoint calls to mind the Stuxnet attack on the Iranian uranium enrichment program. A virus was inserted into the Iranian network, which caused centrifuges to malfunction or self-destruct. But the object of the operation was not merely to interfere with the ongoing program, but also to influence Iranian decision making, as well as American and Russian efforts to limit Iranian nuclear ambitions. This last is evident from the limited duration and destruction of the attack. Those planting the virus could have extended the attack and caused much more damage. Not doing so may have limited Iranian reaction and allowed the attack to function as a warning rather than a declaration of war. The technical, political, and operational sophistication of the operation make it a model of how high-level network-based deception may work. And as such, it indicates the extensive skill set required for success—not merely technical, but also bureaucratic, political, and operational (see Holger Stark’s article, “Stuxnet Virus Opens New Era of Cyber War” at
www.spiegel.de/international/world/0,1518,778912,00.html
). Stuxnet also suggests the extent of training and coordination underpinning the attack, as well as why it has been so difficult for the United States to field a coherent cyber defense strategy.
Just as deception is an essential element of all attacks on networks, so should deception be a constant element in the defense of networks.

Deception: Strategy and Mind-Set
Deception can be used tactically to achieve local ends for transient advantage. It is the magician’s or confidence man’s approach. The advantage sought is immediate and limited in scope. This is the style of deception that might be used in defense of a network to waste a hacker’s time, to discourage a less competent hacker, or, at most, to gather intelligence on the methods of serious hacking. Such limited deceptions have deterrent value. Their frequent exposure, whether due to failure or success, reminds attackers that they can take little for granted. Deterrence is perhaps their primary goal.
Deception, however, may be used to gain more lasting ends. At the highest level, deception may be a metastrategy—that is, a way of unifying action across lines of activity and across time. Here, the objective is to alter the behavior of a serious attacker—individual or organization—to the defender’s advantage.
In a strategic deception, the objective is to control the adversary’s response even after he finally realized he has been had—to transition from a completed operation or a failure toward a success. Most deceptions eventually are discovered or suspected. Rather than cutting the victim off, leaving him to plot his revenge, it would be better to wean him onto another deception—to keep him on the hook or let him down softly. The deception plan must have a concluding Out.
A strategic approach to deception would demand not only more thought, but the highest quality people. The payoff, however, might be orders of magnitude greater in terms of intelligence gained and in defeating not only the proximate attack, but also the attackers and their future attacks.
Deception is too often conceived of as a matter of tricks or fooling the adversary. One could attempt to mystify the intruder/hacker, keeping him in doubt about friendly security plans and intentions. It could even cause him to doubt the effectiveness of his activity.
One also could behave in ways that would leave an adversary mystified without a deliberate attempt to do so. For example, one could constantly change a network’s operating routines, randomize passwords, and change passwords at odd intervals. Mystifying the adversary, however, does nothing to limit or channel his behavior. As an intelligent and motivated adversary, his creativity may lead him to respond in ways the friendly side may not have imagined. Consequently, network defenders may find themselves dealing with situations for which they were unprepared.
8
We do want the adversary to be clear, confident, and wrong when he tries to access protected networks. The intent of deception is to get the adversary to act confidently and predictably. But are we able to provide him the information and/or the incentive to make him so? Seizing and maintaining the initiative is perhaps the most important effect of successful deception. Having the initiative means that the adversary is forced to respond to friendly actions. This can be done by structuring situations such that the outcomes of specific operations create the conditions for subsequent operations. As noted earlier, during research, Vladimir Lefebvre developed a technique called reflexive control. Concerning deception, the essence of reflexive control involves structuring situations such that the victim is led by his personal preferences to behave in certain ways. What does this mean in network defense terms? This is a matter of technical competence and imagination.
Another key to getting others to behave as one wishes them to, against their interest, was provided by Colonel Dudley Clarke. Clarke was instrumental in establishing the British deception organization early in World War II, and then went on to control deception in the Mediterranean. He said that in designing deception, it was necessary to consider what you would tell the enemy commander to do. If you had his ear, what would you tell him? Presumably, you would have in mind what you would do to take advantage of the situation if the adversary complied. The information you would give the adversary is the deception. What you would then do is the exploitation.
9
Successful deception, then, is not the result of applying some set of techniques. It results from paying close attention to the enemy and oneself to divine which of one’s own actions will result in a desired response by an adversary. And, most important, planning how one will take advantage. Without taking advantage, what point is there in deceiving?

Intelligence and Deception
Intelligence
as a noun describes information that has been gathered and processed somehow to make it of practical use to a decision maker. Not all information is intelligence, and information of intelligence value to one decision maker may be irrelevant to another. In order to gather intelligence of use, the gatherers need to have ideas about what information they need to do whatever it is they want to do, or some authority must direct them so that they can sort useful information from everything else. The intelligence collectors must rely on decision makers to tell them what is wanted or, at least, interact with them enough to allow the collectors to inform themselves.
As a process, intelligence requires prioritization. Resources are never sufficient to gather everything—all that might be useful or interesting. Prioritization exacerbates the uncertainty of intelligence gathered to support competitive activity. That is what defending networks is about by definition. That which makes items of information attractive to adversary collectors makes them attractive to defenders.
Intelligence is of two kinds:
Positive intelligence (PI) is information gathered to facilitate one’s own side achieving its ends.
Counterintelligence (CI) is information gathered to prevent adversaries from compromising network defenses or defenders. A subset of CI called offensive CI seeks out and tries to penetrate hostile elements for the purpose of compromising or destroying at least the effectiveness of the adversary himself.