Reverse Deception: Organized Cyber Threat Counter-Exploitation (105 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

Vector Summary
The previous discussions have only touched on some of the many vectors that may be of use in profiling malicious online actors. Each of these areas should be pursued in depth to provide a better picture of the attackers and their motivations, in order to find clues to their identities.
An example of another potentially useful profiling vector is the application of linguistics and semiotics to communications made by hacking gang members. This may provide some probabilistic predictions for basic demographics of the individual, such as gender, age, educational attainment, ethnicity, and geolocation. Additionally, cataloging word frequencies, phrases, and other unique speech or text fragments in a database can assist in the identification of individuals of interest and help an investigation narrow its focus to a smaller set of targeted individuals. The application of concepts and principles from linguistics and semiotics may also be useful in determining the level of threat that someone represents, such as the WarmTouch system developed by Shaw and Stroz.
6
Whatever profiling vectors are selected, when the profiler or analyst constructs a description of a targeted individual or individuals using multiple vectors or dimensions, the resultant profile, when combined with other forensic evidence provided by investigators, can often provide a much more complete picture of individuals pursuing advanced and persistent threats.

Strategic Application of Profiling Techniques
Now we turn from the analysis and construction of profiles for groups or individuals to profiles of the hacking community as a whole. Understanding how the social structure of the hacking community is changing can provide strategic analysts with a better understanding of how the cyber threat matrix may change in the future, and how members may migrate to and from other groups, such as cyber criminal gangs. Analysts can also gain enough understanding of the social forces involved to be able to build realistic future potential threat scenarios. These types of objectives support longer-term objectives that include areas such as proactive defenses, resource planning, and developing legislative and governmental policies that address the contingencies of emerging cyber threats.

Example Study: The Changing Social Structure of the Hacking Community
One of the early attempts to analyze the social structure of the hacking community was conducted by Kilger and his colleagues (Kilger et al, 2004). This analysis was driven by the application of a hybrid qualitative/quantitative research methodology to uncover the hidden social dimensions within the hacking community. The investigation used a contextual analysis of the Jargon File as it existed online in 1994.
The Jargon File was an accumulation of a large number of words and phrases that had special meaning within the hacking community.
7
It was maintained and updated by a series of caretakers, with its gradual demise sometime after 2003. There were never proven accusations of malfeasance in the manner in which the file was being maintained. The analysis of the Jargon File identified 18 social dimensions within the hacking community, which included, but were not limited to, technology, derogatory, history, status, and magic/religion. The incidence of thematic terms suggests to some extent the importance of the social dimension within the community itself.
This study was repeated again a number of years later using one of the last versions of the Jargon File in 2003, around the time that conflicts among its various caretakers and proponents effectively ended its community-wide acceptance (Kilger, 2010). The objective of the replication was to be able to compare the social structure of the hacking community between two periods of time. Given the swift rate at which technology and the community itself is evolving, the nine-year time window between the two studies should be sufficient to detect changes in the social structure.
Figure 10-5
shows the distributions of the social dimensions embedded within the hacking community for 1994 and the reanalysis of data from 2003. Examining the data over this period shows some significant changes within the hacking community’s social structure. In the following sections, we’ll look at the technology, derogatory, and magic/religious dimensions in more detail.
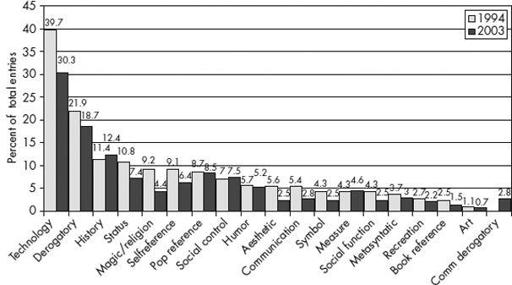
Figure 10-5
Dimensions of the social structure of the hacking community
Technology
Technology obviously plays a key role in the community, and this can be seen by its ranking as the social dimension with the most terms and phrases associated with it in the Jargon File. While this statement is true for both time periods under investigation, it can be seen that there has been a substantial drop in the incidence of this dimension.
It’s very likely not the case that the rate of introduction of new technical terms has significantly decreased given the evolving nature of the field. What does seem to be the case is that there is less focus on technology and technical terms than in the past. While the interpretation of this shift is not entirely clear, part of it may be due to several factors, including an influx of individuals into the hacking community who lacked some of the professional engineering training and background that was more prevalent in the field in 1994.
Derogatory
The second important dimension found in the analysis is the derogatory dimension. Derogatory terms have historically been used by members of the hacking community as elements of social-control processes within the community. For example, when status conflicts arose from issues such as challenges to claimed skill levels, derogatory terms were utilized as social-control mechanisms to attempt to resolve those conflicts. Terms such as “luser” and “lamer” were dispatched in an effort to disparage the individual making allegedly false or overinflated skill or expertise claims.
Notice in the time that has elapsed since the first study there has also been a decrease in the number of derogatory terms within the hacking subculture. Perhaps this is due to a moderate deemphasis on technical skills within the community, which would correlate with the decrease in technology terms. Or perhaps it is the cumulative effects of the rise in popularity and attendance at hacker conferences. Remember that these status conflicts arise more often online than offline because of the limited bandwidth that is normally used for communications among members of the hacking community (such as e-mail and IRC chat rooms). As more and more members of the community meet face-to-face where these communication constraints are absent, it may be the case that more status conflicts within the hacking community are being resolved, and thus the need for additional derogatory terms and phrases within the community shrinks accordingly. This hypothesis may receive a bit of further support when one looks at the social dimension of status within the hacking community. There is a fairly significant decline in the incidence of status-related terms and phrases in the Jargon File between 1994 and 2003.
Magic/Religion
One of the most telling shifts in the social structure of the hacking community is reflected in the more than 50 percent decline in the number of terms that are associated with magic/religion. The concepts of magic and religion have been present and important core social elements in the hacking community since its early beginnings.
8
Magic/religion might at first glance seem like an unlikely key element in the social structure given its technical nature. However, it is in fact due to the complex nature of the technology at the heart of the industry that this concept is present and plays such a key role in the original core spirit of the hacking community.
One way to explain this dimension is to imagine some object A—for this example, some operating system shell command with various parameters. Suppose that the hacker issues the command to the operating system, and the result of that command is event B. If the hacker cannot logically explain why command A resulted in event B—that is, the complex operating system functions as a black box—then one way to look at the phenomenon is as the result of magic. This emergence of a belief in magic is not unlike similar studies in the anthropology literature, where members of an indigenous tribe use magic to explain the reason for certain phenomena occurring in the natural world around them.
Especially during the early days of the hacking community, operating systems and their internals were rather cryptic, and the reasons for following specific procedures were mystical at times.
9
There arose a need to develop a Zen-like attitude toward operating and maintaining complex and often cantankerous operating systems. This nurtured a sense of magic about the relationship between system administrators and the servers in their care. Unix wizards, as they came to be known, were people who knew incredible amounts about the operating systems and hardware, and were revered for being able to help their fellow, less-experienced system administrator friends out of serious jams. Many times, the wizard would guide the panicked system administrator through a series of procedures to resolve the issue, but would refuse to explain the logic behind the rescue, preferring instead to label it magic. Everyone had a wizard they could call on in those days. The need to rely on those wizards generated strong social bonds between many individuals in the hacking community.
The system administration environment has changed dramatically since those early days. While operating systems are more complex than ever, the prevalence of graphical user interfaces and gigabytes of online technical resources diminish the original social dimension of magic. Instead of calling wizards with whom they have personal relationships, corporate system administrators call outsourced technical support professionals, often halfway around the world. The shifts in these technologies and practices have greatly diminished the role of magic/religion within the technical community, and the disparity between the incidence of magical/religious terms between the years 1994 and 2003 provides further evidence of this decline.
