Cyber Warfare (4 page)
Authors: Bobby Akart

Cyber attacks of varying degrees of destruction occur daily from a variety of actors. Some of the more recent high-profile attacks result from retail data breaches. The Sony Pictures Entertainment hack, website vandalism and distributed denial-of-service (DDoS) attacks are all examples of data breaches.
The groundwork is set for what is a cyberattack and the environment, cyberspace, in which they are launched and experienced by the victim. This is the first step in dispelling myths to understand risk and what is possible—and not possible—when it comes to protecting your firm and the nation.
Now the real fun begins – we’ll dissect the four most commonly confused terms:
cyber-terrorism
,
cyber vandalism
,
cyber espionage
and
cyber war
. The objective is to dispel myths and, by establishing a shared understanding, provide a way for managers to cut to the chase and understand risk without all the FUD. The graph below shows the four terms and attributes at a glance.
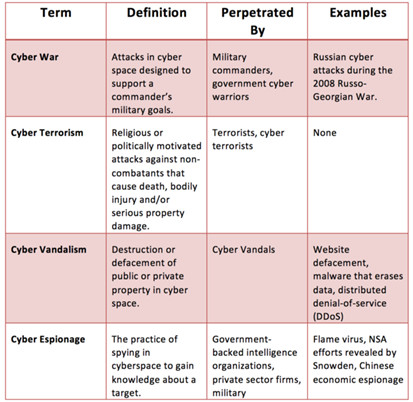
Now let’s dig into each definition and examine the fundamentals.
Cyber Terrorism
No one can agree on the appropriate definition of terrorism, and as such, the definition of cyber terrorism is even murkier. Ron Dick, director of the National Infrastructure Protection Center, defines cyber terrorism as a criminal act perpetrated through computers resulting in violence, death, and destruction, and creating terror for the purpose of coercing a government to change its policies.
Many have argued that cyber terrorism does not exist because
cyberspace
is an abstract concept. On the other hand, terror in a shopping mall is a very real, quantifiable event that can lead to bodily harm for the average citizen. Cyber terrorism, as a term, has been used (and misused) so many times to describe a cyber attack, it has almost lost the impact its real world counterpart maintains.
According to US Code, Title 22, Chapter 38 § 2656f, terrorism is defined as
premeditated, politically motivated violence perpetrated against non-combatant targets by subnational groups or clandestine agents
.
By definition, a cyber terrorist attack must include violence toward non-combatants and result in large-scale damage or financial harm. Furthermore, it can often be difficult to attribute motivations, goals and affiliations to cyber attacks, which makes attribution and labels difficult in the cases of both accepted acts of terrorism and cyber terrorism.
Based on publically available knowledge, there are no known examples of cyber terrorism. It will happen – it just hasn’t happened yet.
Cyber Vandalism
There is not an
official
U.S. government definition of cyber vandalism, although the terminology has been used by the President at times. Supreme Court Justice Potter Stewart opined precise terminology may not be easy to describe, but
you will know it when you see it
.
The traditional definition of
vandalism
from the Merriam-Webster dictionary is the
willful or malicious destruction or defacement of public or private property
.
Cyber vandals usually perpetrate an attack for personal enjoyment or to increase their stature within a group, club or organization. They also act very overtly, wishing to leave a calling card, so the victim and others may assign responsibility. Some conventional methods are website defacement, denial-of-service attacks, forced system outages and data destruction.
Here is an example from the hacktivist group Anonymous.

The following are a few examples of cyber vandalism from Wikipedia:
Anonymous DDoS attacks on various targets in 2011-2012
Operation Payback was a coordinated group of attacks on high-profile opponents of music and video file sharing. Operation Payback was orchestrated by Anonymous utilizing distributed denial of service (DDoS) attacks on torrent sites—websites that contain metadata about files and folders spread over a vast number of networks. File-sharing proponents decided to launch DDoS attacks on the most vocal piracy opponents. The initial reaction snowballed into a wave of attacks on major pro-copyright and anti-piracy organizations, law firms, and individuals.
Lizard Squad DDoS attacks and website defacements in 2014
The Lizard Squad is a black hat hacking group, mainly known for their claims of distributed denial-of-service (DDoS) attacks primarily to disrupt interactive gaming related services.
On September 3, 2014, Lizard Squad falsely announced that it had disbanded only to return later on, claiming responsibility for a variety of attacks on prominent websites during the holiday season. Victims included the Sony PlayStation Network, the Xbox Live network, and online gaming participants of League of Legends and Destiny.
Sony Pictures Entertainment in November 2014
The Sony Pictures Entertainment hack was a release of confidential data belonging to Sony Pictures Entertainment on November 24, 2014. The data included personal information about Sony Pictures employees and their families, e-mails between employees, information about executive salaries at the company, copies of previously unreleased Sony films, and other information. The hackers called themselves the
Guardians of Peace
and demanded the cancelation of the planned release of the movie
The Interview
, a comedy about a plot to assassinate North Korean leader Kim Jong-un. United States intelligence officials, evaluating the software, techniques, and network sources used in the hack, allege that the attack was sponsored by North Korea. Naturally, North Korea has denied all responsibility, and some cybersecurity experts have cast doubt on the evidence, alternatively proposing that current or former Sony Pictures employees may have been involved in the hack.
The Sony Pictures case is an excellent example of the problems of attribution. The United States government, which quickly referred to the Sony attack as cyber vandalism, launched an intense investigation and were still unable to point a finger of blame.
Cyber Espionage
Much of what the public, politicians or security vendors attribute to
cyber-terrorism
or
cyber war
is
cyber espionage
, a real and quantifiable type of cyber attack that offers plenty of legitimate examples. An eloquent definition comes from James Clapper, Director of National Intelligence in which he refers to cyber espionage as
intrusions into networks to access sensitive diplomatic, military, or economic information
.
There have been several high-profile cases in which hackers, sanctioned by the Chinese government, infiltrated US companies, including Google and The New York Times, with the intention of stealing corporate secrets from firms that operate in business sectors in which China lags behind. These are examples of corporate or economic espionage, and there are many more players – not just China.
Cyber spies also work in a manner similar to the methods used throughout history. Sun-Tzu infiltrated his military opponents with moles. Undercover espionage was prevalent during the Greek and Roman empires and were employed by ancient governments to further political goals and information gathering. Many examples exist, from propaganda campaigns to malware that has been specifically targeted against an adversary’s computing equipment.
For example, the Flame virus is a very sophisticated malware package that records through a PC’s microphones, takes screenshots, eavesdrops on Skype conversations, and sniffs network traffic. Iran and other Middle East countries were targeted until the malware was discovered and made public. The United States is suspected as the perpetrator.
After WikiLeaks, the Snowden documents revealed many eavesdropping and espionage programs perpetrated against both US citizens and adversaries abroad by the NSA. The programs, too numerous to name here, are broad and use a wide variety of methods and technologies.
Cyber Warfare
Nineteenth-century Prussian general and military theorist Carl von Clausewitz stated,
War is a mere continuation of policy by other means
. Today, rogue nations and a number of private actors use cyber intrusions as a means of attaining policy goals. These goals often include stealing sensitive corporate data, disrupting information technology systems, and reconnoitering the cyber networks of potential military adversaries. In the same way that ships patrolling coastal waters or infantry prodding along ill-defined borders risked sparking conflict throughout modern history, today’s aggressive use of cyber warfare has led to diplomatic clashes, and the threat of escalation.
Cyber warfare, utilizing the Clausewitz theories, is the use of computers by a nation state for an extended, cross-sector interruption of an opponent’s activities, especially through the use of deliberate attacks on their information technology or critical infrastructure systems. This definition excludes minor acts of cyber vandalism such as DDoS attacks, and also the collection of information from the adversaries’ network systems.
Due to the lack of a broadly accepted definition via an international treaty or established set of guidelines, limiting the definition of cyber warfare is the norm. At the same time it’s challenging because definitions can’t cover every contingency and are of limited use in gray areas.
International organizations and governments have taken various and often cryptic steps to try to define doctrine for their self-serving approach to cyber war.
A recently published NATO manual on the applicability of international law to cyber warfare does not explicitly define the term, although it does distinguish between
cyber warfare
and
cyber operations
. In it
, cyber weapons
are defined as those that can destroy objects and injure or kill people. Recently a NATO official said a cyber attack on one NATO member could be treated as the equivalent of an armed attack that will be responded to by all NATO allies. But the nature of the NATO response will be decided by allies on a case-by-case basis.
President Obama in 2013 issued a classified Presidential Policy Directive that authorizes military and intelligence agencies to identify likely overseas targets for U.S. cyber attacks. The document permits military commanders to launch cyber attacks to respond to the
threat of an imminent attack
or an emergency situation.
Apparently, the U.S. is following the lead of the Israelis. The Israeli Defense Forces say their military directives handle the event in cyberspace
similarly to other battlefields on the ground, at sea, in the air, and space
. Israel acknowledges that it engages in cyber activity consistently and relentlessly, gathering intelligence and defending its cyberspace. The IDF unabashedly states it is prepared to use cyber space if necessary to execute attacks and intelligence operations—both in defense and part of its military capabilities.
For more than ten years, China’s military doctrine has been relatively explicit on the issue of cyber warfare. China sees the use of cyber intelligence as a methodology whose primary purpose is
to seize and maintain information dominance
. Chinese military tacticians recommend the use of cyber weapons to deceive the enemy or apply psychological pressure on its adversaries.
Russian operations in this area reflect a desire to disrupt information systems of a nation-state while engaging in a disinformation campaign. Russian definitions avoid the term
cyber
. This Russian semantics may indicate a preference for establishing control of internal and external messaging on issues of importance to Moscow. The importance of their messaging became evident in the Russia-Georgia border war of 2007.
Chapter Two
Recent Cyber Skirmishes
A nation’s intelligence services use cyber tools to conduct the sort of sensitive tasks that, until recently, were carried out by more traditional means of espionage—spies, commandos, or missiles. Two examples indicate how such actions can disrupt military and economic infrastructure as efficiently as kinetic strikes.