Cyber Warfare (15 page)
Authors: Bobby Akart

“Our National Grid is coming under cyber-attack not just day-by-day but minute-by-minute,” said James Arbuthnot, a member of the British Parliament whose committee scrutinized the country’s security policy. “There are, at the National Grid, people of very high quality who recognize the risks that these attacks pose, and who are fighting them off, but we can’t expect them to fend them off forever.”
The power grid is a vital system for our society, and the cyber strategy of every government must consider its protection a high priority, a terror attack would leave entire countries sitting in the dark. Several high profile cyber security firms have issued a hypothetical attack scenario and estimation of the losses—both of loss of life and economically.
What will happen in the case of a cyber-attack on a critical infrastructure in the US? What is the economic impact of a cyber-attack against America’s power grid?
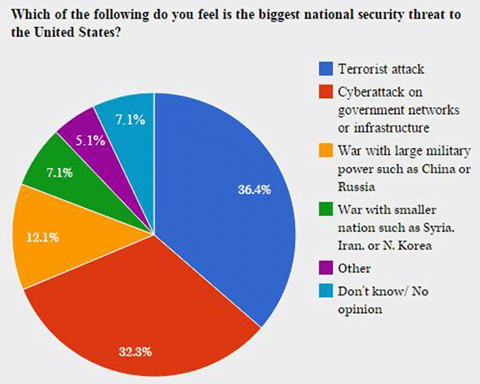
According to a poll of 2,173 registered voters by researchers at the Morning Consult firm, cyber attacks rank a close second to a terrorist attack on the list of biggest threats to the United States. The research showed that cyber security experts estimate the insurance industry could face losses of over twenty billion dollars.
Specifically, thirty-six percent of voters consider acts of terrorism at the top of a list of major security threats, followed by cyber attacks at thirty-two percent.
Lloyd’s of London conducted a very in-depth study in 2015,
Business Blackout
that describes the impacts of a possible cyber attack on the nation’s critical infrastructure. It is the first time that the insurance industry has elaborated on a similar report. According to the report prepared by Lloyd’s in a joint effort with the University of Cambridge’s Centre for Risk Studies, a devastating cyber attack on America’s power grid would have a catastrophic impact on multiple types of insurance.
The attack scenario described by
Business Blackout
illustrates the effects of a hypothetical malware-based attack on systems that controls the U.S. power grid. In their hypothetical scenario, the attack causes an electrical blackout that plunges fifteen U.S. states and highly populated cities, including New York and Washington, into darkness. Nearly 93 million people will be affected without power in the hypothetical.
According to the researchers, the attack will cause health and safety systems to fail, disrupting water supplies as electric pumps fail. The chaos will reign causing the failure of central services, including transportation. Because the malware can infect the Internet, thereby allowing it to search and compromise fifty generators that it will destroy, there would be lengthy power outages in the region.
The total of claims paid by the insurance industry has been estimated to be included in the interval comprised between twenty and seventy billion dollars depending on the length of time necessary to remedy the scenarios designed by the researchers.
The researchers involved in the simulation have calculated the economic losses could approach $1 trillion, depending on the number of components in the power grid compromised by the attack.
Economic impacts included in the report were direct damage to assets and infrastructure, the decline in sales revenue to electricity supply companies, loss of sales revenue to business and disruption to the supply chain. In order to form their hypothesis, the experts analyzed the historical outages, estimating that currently the power interruptions, the vast majority of which last five minutes or less, already cost the US about $96 billion.The business and industrial sectors are the sectors most impacted by the attack on the power grid due to their dependency on electricity.
The Business Blackout report states evidence from historical outages, and indicative modeling suggests that power interruptions already cost the US economy roughly one hundred billion dollars a year. Under normal conditions, over ninety-five percent of outage costs are borne by the commercial and industrial sectors due to the high dependence on electricity as an input factor of production.
As explained in the report, it is important to identify the risks related to a possible cyber attack and adopt all the necessary measures to mitigate them. The protection of critical infrastructure like a power grid should be an essential part of the cyber strategy of any government.
Threat intelligence and information sharing are essential to limit the number of cyber attacks. As a result of increased awareness and recent cyber events, President Obama issued an
Executive Order Promoting Private Sector Cybersecurity Information Sharing
, confirming the administration’s cyber strategy. Toward that end, in 2014 the U.S. Government issued the
Framework for Improving Critical Infrastructure Security
.
The
Framework
was published in response to Executive Order 13636, which states that “it is the Policy of the United States to enhance the security and resilience of the Nation’s critical infrastructure and to maintain a cyber environment that encourages efficiency, innovation, and economic prosperity while promoting safety, security, business confidentiality, privacy, and civil liberties.”
The
Framework
was designed to improve security for IT and SCADA networks deployed in sensitive industries such as energy, water, and financial services. The
Framework
stresses the information sharing on principal threats and outlines and defines the best practices that allow mitigation of the attacks. Both private and public sector organizations are encouraged to report any suspect activity for prevention and a prompt response to the incidents. The implementation of the
Framework
is in its infancy. Thus there has been little written about its success.
Chapter Seventeen
Based upon what we know, could hackers bring down the U.S. Power Grid?
It has been clearly established that various threat actors around the world have made it their goal to inflict maximum pain on the United States and one method that can be utilized is a grid down scenario, whether by electromagnetic pulse weapon, or cyber attack. The biggest fear of many political leaders and cyber security analysts, the worst case scenario, is often described in terms of a cyber attack on our critical infrastructure. These cyber war predictions almost always envision an attack on the U.S. power grid that would cause a widespread blackout.
The nation states who currently have the greatest capability to use cyber attacks to inflict broad, systemic damage on their adversaries are the well-resourced nation states who are most likely to calibrate their targeting carefully. For example, if China or the United States were to try to immobilize the entire economy of the other, they would open a serious risk of a cyber retaliation aimed at inflicting the same kind of damage, or worse. This is similar to the
mutually assured destruction
doctrine that helped restrain the use of nuclear weapons. But yet the risk remains because, in the cyber realm, the bad actors may have nothing to lose. Think North Korea.
In 2014 testimony before the House Intelligence Committee, NSA Director Admiral Michael Rogers went into some detail on those risks:
Admiral Rogers was questioned about one such hypothetical. “If it was determined that malware was on those critical infrastructure systems, can you be a little more definitive about what does that mean? If I’m on that system, and I want to do some harm, what does that do? Do the lights go out? Do we stop pumping water? What does that mean? And the fact that it was there does that mean they already have the capability to ‘flip the switch’ if they wanted to?”
Admiral Rogers responded: “Well let me address the last part first. There shouldn’t be any doubt in our minds that there are nation-states and groups out there that have the capability to do that. To enter our systems, to enter those industrial control systems, and to shut down, forestall our ability to operate, our basic infrastructure. Whether it’s generating power across this nation, or whether it’s moving water and fuel, once you’re into the system and you’re able to do manipulate that. It enables you to do things like, if I want to tell power turbines to go offline and stop generating power, you can do that. If I wanted to segment the transmission system so that you couldn’t distribute the power that was coming out of the power stations, this would enable you to do that. It allows you to shut down very segmented, very tailored parts of our infrastructure.”
A number of media outlets and cyber security professionals interpreted these comments as a claim by the NSA that a country like China could take down our nation’s power grid. Is a widespread, national blackout caused by hackers a realistic possibility? The power grid is vulnerable to attack. Adm. Rogers’ testimony was extremely important as it provided a strong, authoritative voice to what is an urgent problem facing this country right now—
America’s critical infrastructure is vulnerable to attack, it’s a complicated problem to fix, and an attack is imminent.
PART SEVEN
Preparing For Cyber Warfare

Chapter Eighteen
Cyber War Implications for Business
Cybergeddon or World War C is not here yet, but it might be tomorrow. You never know when the day before—is the day before.
Under the most likely scenarios, the effects of a cyber war on most businesses are more likely to be disruptive than apocalyptic for two main reasons. Cyber intrusions can immobilize your business operations for hours and maybe days. Modern critical infrastructures tend to have enough built-in stop-gap measures and protections to prevent a cataclysmic crash of the entire power grid simultaneously or for an extended period.
The business of cyber terrorism is growing in many directions. There is a growing gray market for cyber weapons able to exact more powerful exploits—directed against utility and industrial control systems. These hacking tools are becoming more readily available to governments of smaller nations and even non-state groups, like ISIS, that would have less to lose in a cyber exchange than a major power. In addition, the number of potential targets of hacker activity is growing exponentially as technological advances allow interconnectivity of networks subject to being targeted.
The accelerating globalization of many business entities will also leave them increasingly vulnerable to disruption from cyber war even if it does not involve their home government. The public sector relies on R&D and manufacturing that are often based in third-world countries. These important sources of innovation and revenue could be cut off, at least temporarily, by the deployment of cyber weapons. Cyber war operations could also disrupt supply chains and support services. Tensions between China and other nations in Southeast Asia could disrupt call center operations in India or the manufacture of specialty parts for global supply chains in the Philippines.
A cyber war could disrupt business operations across much of the United States economy. Industries closely tied to military capabilities would quickly become the front lines of such a conflict. The defense industry, airlines, energy companies, pharmaceutical manufacturers and healthcare providers, commercial Internet service providers and telecommunications firms are just a few of the industries that serve military and other government operations. Then there are the utilities that supply power and water to government facilities.
Business, nonprofit, and government leaders should anticipate significant indirect effects. Companies around the world could experience damage from malware or a massive DDoS attack that a hacker introduced into their business networks via customers, suppliers, perhaps even employees’ personal contacts and electronic devices that had been connected to other corporate networks. As the world becomes more interconnected, the threat of cyber intrusion grows.
A cyber war—like any war—is an outcome no one wants. But, given the ready availability and growing power of cyber weapons, the plethora of potential military targets on IT networks, and the many points of friction between competing nation states, this is an outcome we could all soon face with little or no warning. Organizations of all kinds need to be able to protect their most valuable assets when a cyber war comes or their business will risk becoming collateral damage.